Release Notes
The latest releases to the Method platform.
January 13, 2026
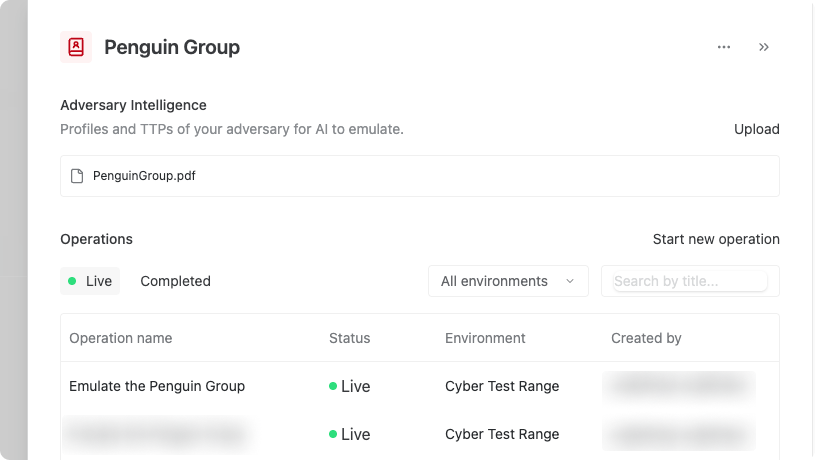
Overwatch lets you run operations from your command line, with recording, collaboration, and reporting in Method
Overwatch is a cross-platform CLI that allows you to run operations from your own terminal with collaboration and reporting capabilities powered by the Method platform.
Overwatch records terminal sessions, showing your command history in Method to power an easy search, filtering, and one-click Report generation experience.
Method also enables multiple users on different machines to collaborate on a single Overwatch session, with the option to join the same session or to watch a teammate work.
Overwatch will soon be integrated in Operator, making it easy to switch between Operator’s easy, UI-driven red team experience and Overwatch’s more flexible command line driven experience.
Start a new Overwatch session by navigating to Reaper and clicking New in the top-right corner.
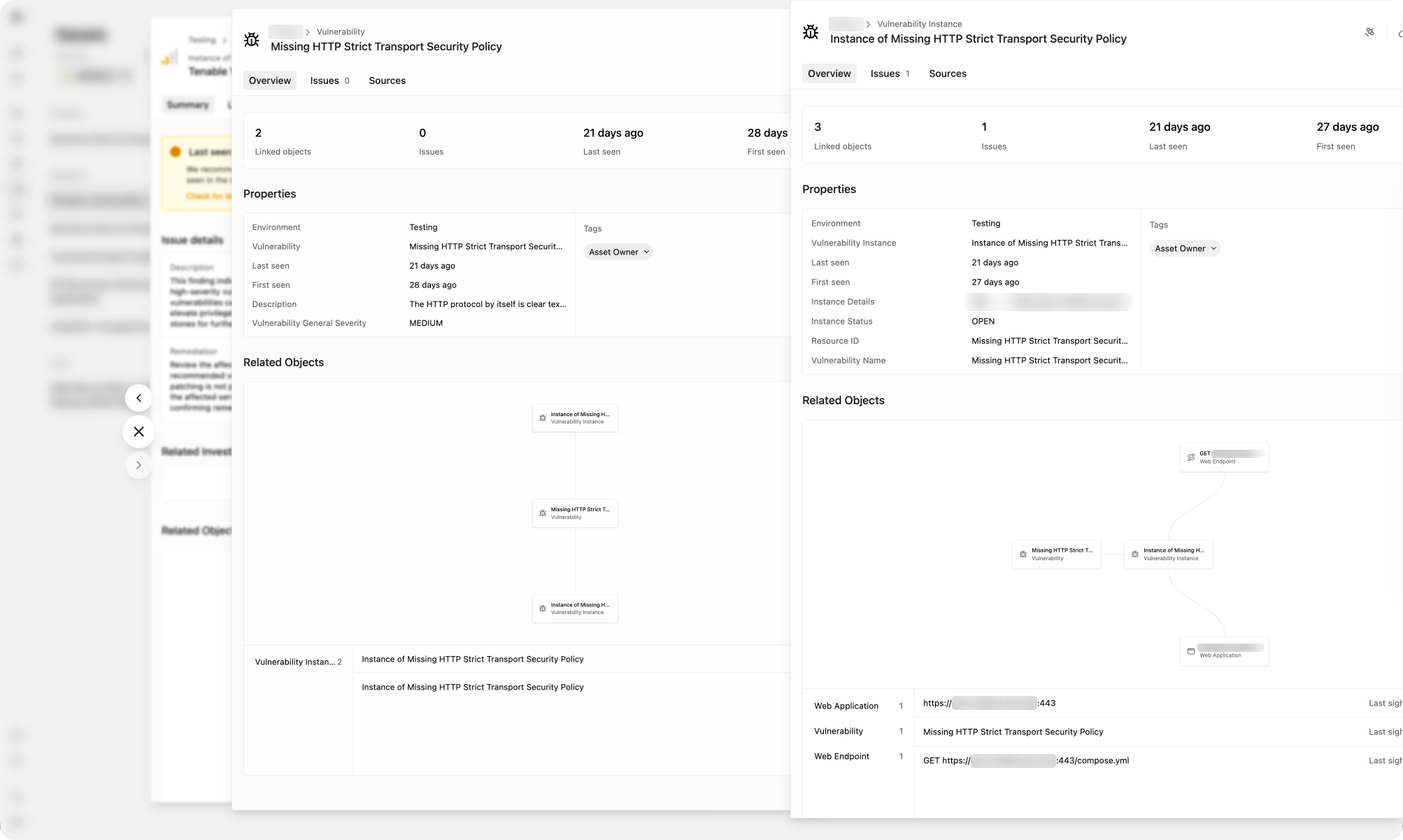
View Tenable vulnerability data in Method
Method now integrates Tenable’s vulnerability data into Method’s object model. Method builds unified views of your exposures, misconfigurations, vulnerabilities, spanning across Tenable and Method scans in Bastion, giving you a thorough understanding of risk across your estate.
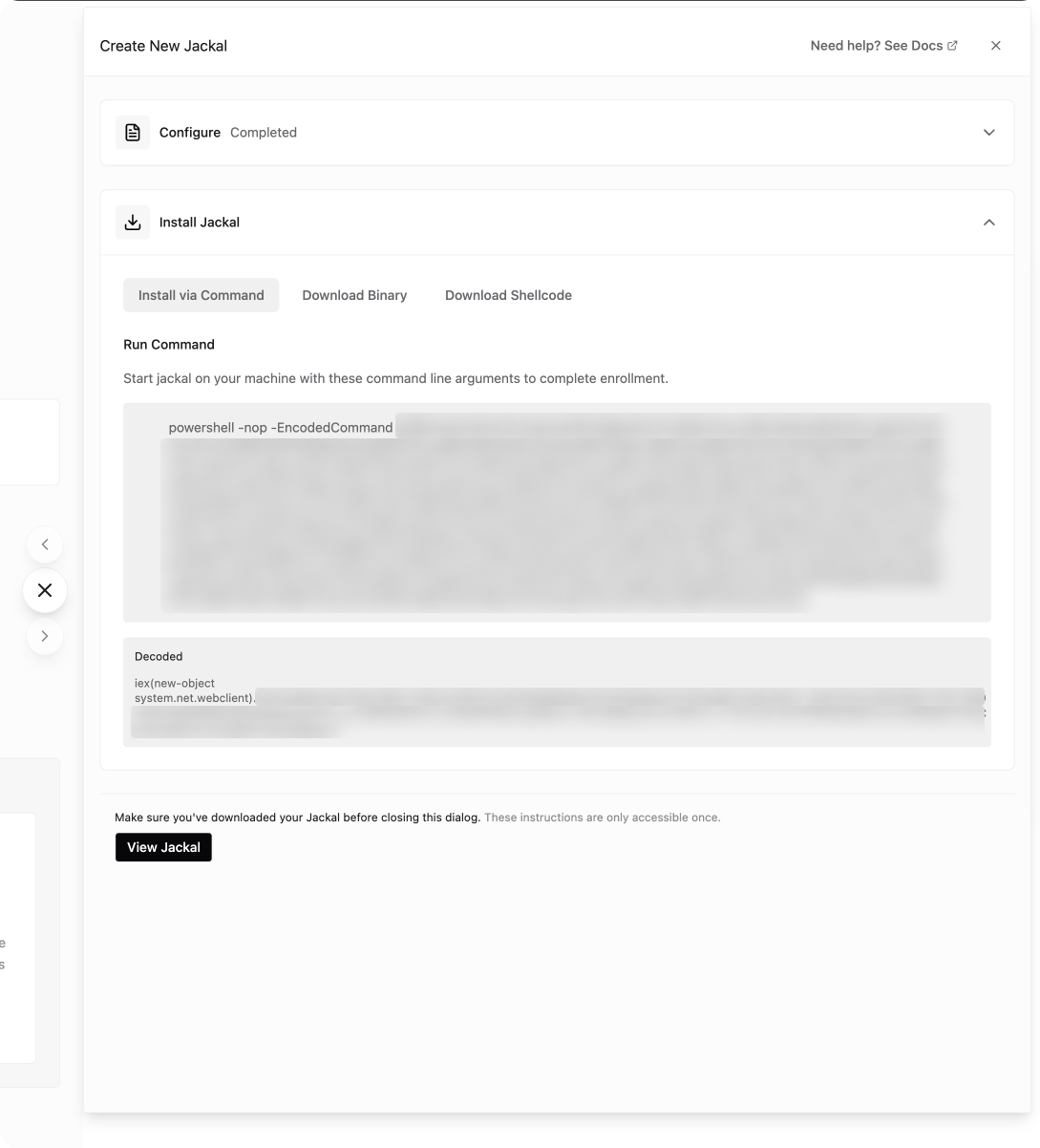
More ways to install Jackal agents
Method’s Jackal agents now have more fine-grained deployment parameters and multiple options to install. Installing a Jackal used to require downloading and installing a binary, then configuring it in the Method platform after coming online for the first time.
Now, Jackals can be installed using a single command and supports multiple execution modes, such as on-disk or in-memory.
The following tools have been released or updated. You can view them in the Tools app and Operator app in Method.
- New: WinRM Jackal Drop deploys a Jackal agent to a remote host via WinRM.
- Updated: tools that accept Credentials now have configuration presets. These presets allow the user to choose between different strategies for choosing sets of input credentials based on upstream data in the Operation or Automation.
- Updated: The Password Spray tool is now split into Domain Password Spray and Network Service Password Spray to allow for greater control over target-password pairings.
December 1, 2025
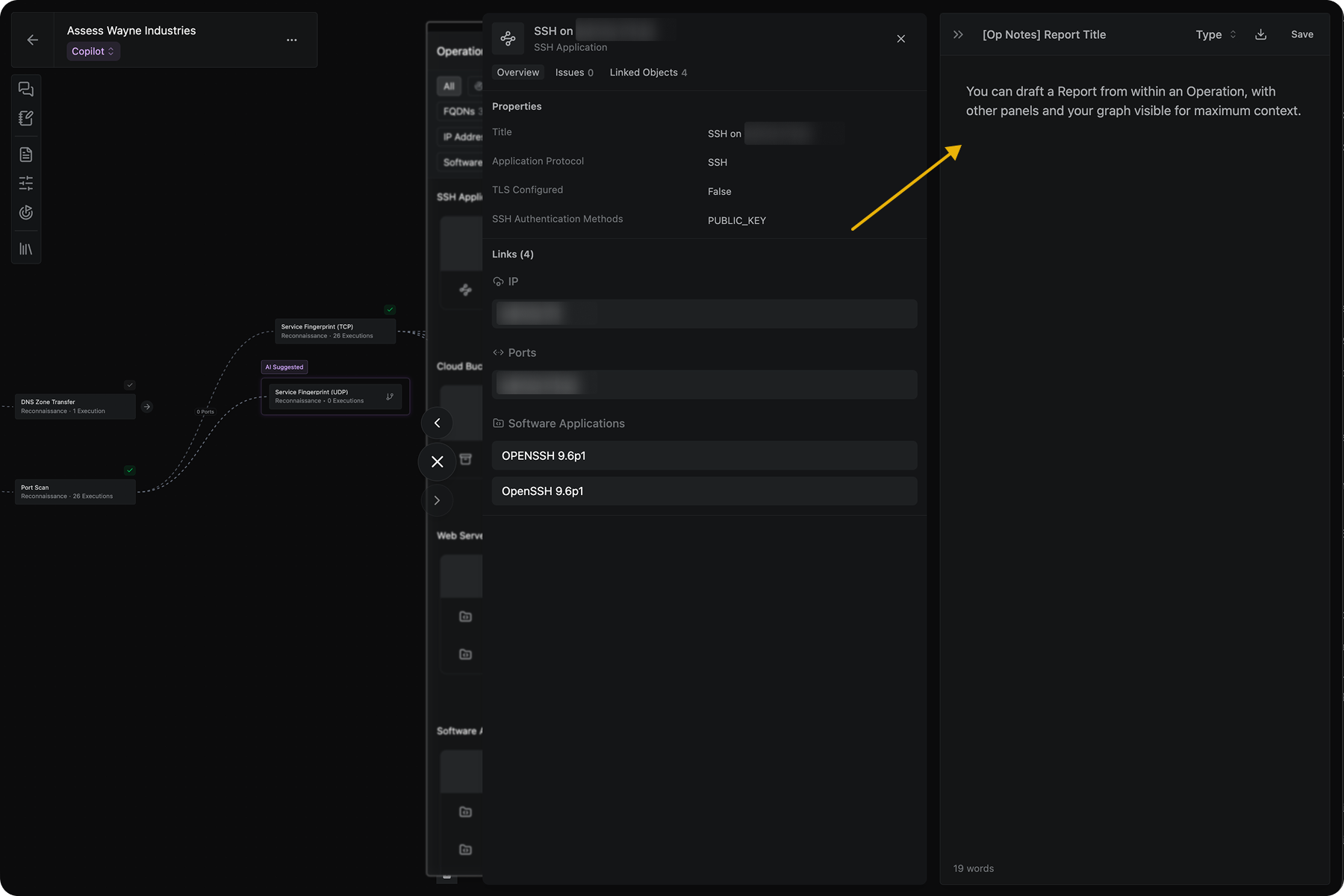
Write Operation Notes and After Action Reports directly in Operator
You can now create and edit a Report in Operator, allowing you to easily draft your operation notes and after-action reports with the context of your Operation easily accessible.
Add details from any part of your operation like tool executions, discovered assets, or Issues to your Report with couple of clicks. Like all Method Reports, these can be exported to PDF for off-platform sharing and discussion.
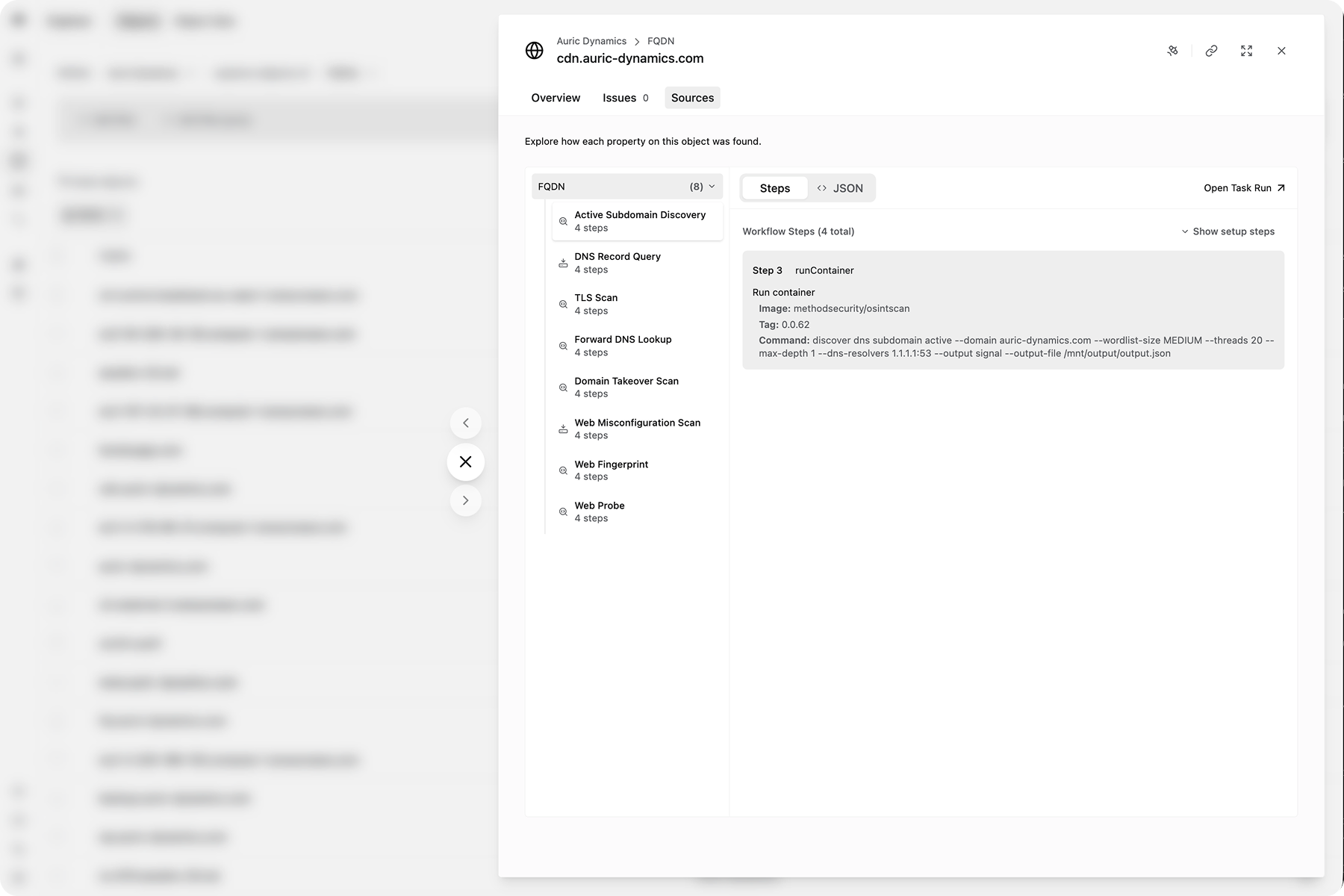
Object provenance is easier to understand with Object Sources
Investigate new asset discoveries with Object Sources. Objects now show sources for each property allowing you to see which tools and inputs generated it. On an Object view, navigate to the Sources tab to see every property on the object along with all of the ways its properties were discovered.
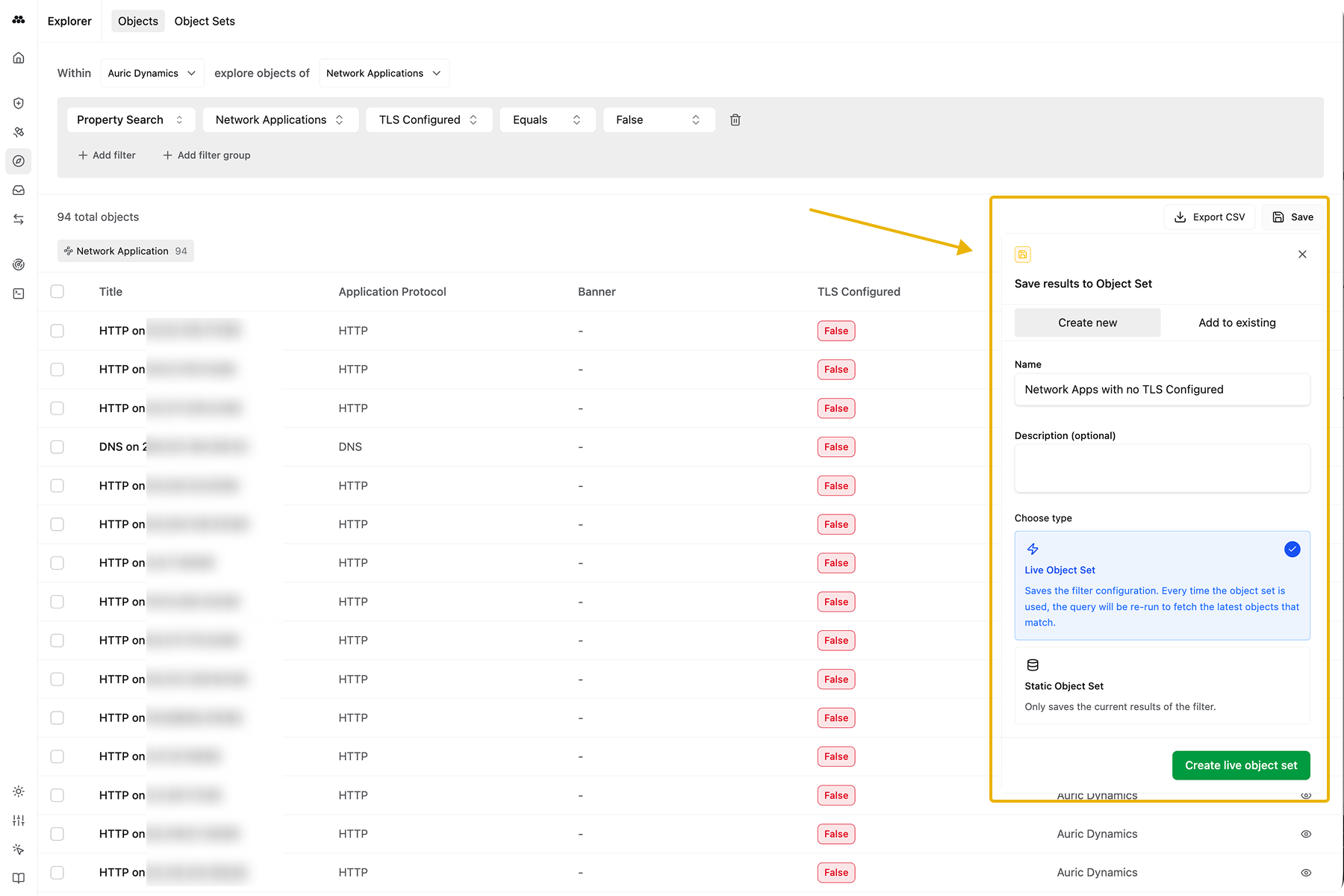
Objects are easier to organize and action with Object Sets
Organize and monitor important subsets of your assets using Object Sets. An Object Set is a manually or dynamically constructed list of Objects you care about.
They can be manually curated, for hand-curating your inventory into lists like “Critical FQDNs” or “Important Web Applications” to monitor them for Issues. They can also be automatically generated and updated, allowing you to create sets of filters and see your assets that meet those criteria. Object Sets can be created and explored in Explorer.
This is just the beginning for Object Sets. Soon you’ll be able to use them as a launching off point for automated scans in Bastion, Operations in Reaper, and more detailed views in Explorer.
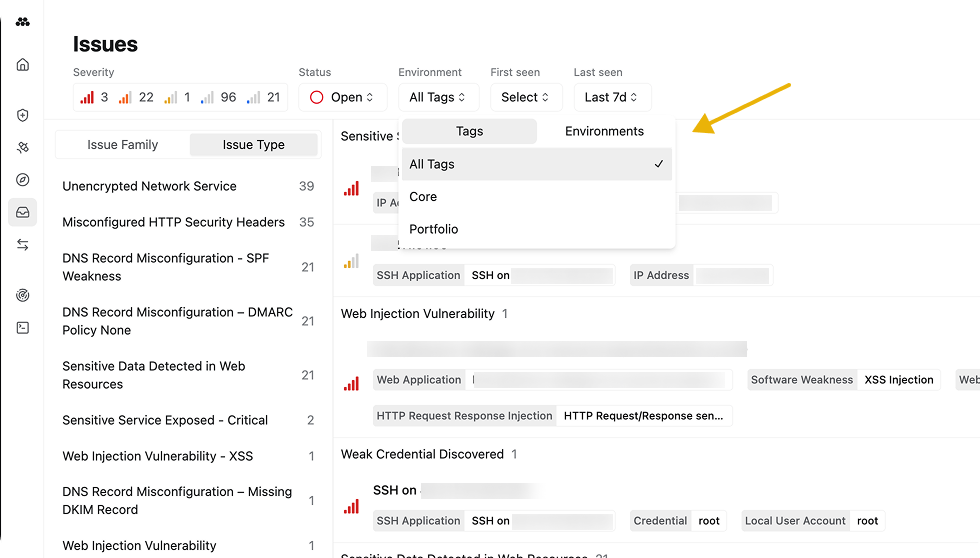
Flexibly draw boundaries around areas of responsibility using Environment Tags
Environment Tags can now be managed directly in the UI, enabling organizations with high scale to flexibly organize the environments they defend into themed sub-groups without needing the help of a Method representative.
Environment Tags are used to filter the scope of the Bastion dashboard and the Issue Inbox and get a more granular understanding of risk within specific subsets of your organization.

Environment tags can be used to organize environments into any logical grouping – their relationship to the main org, their location, the type of environment, and more. Now, you can create and manage the tags yourself in the Admin app.
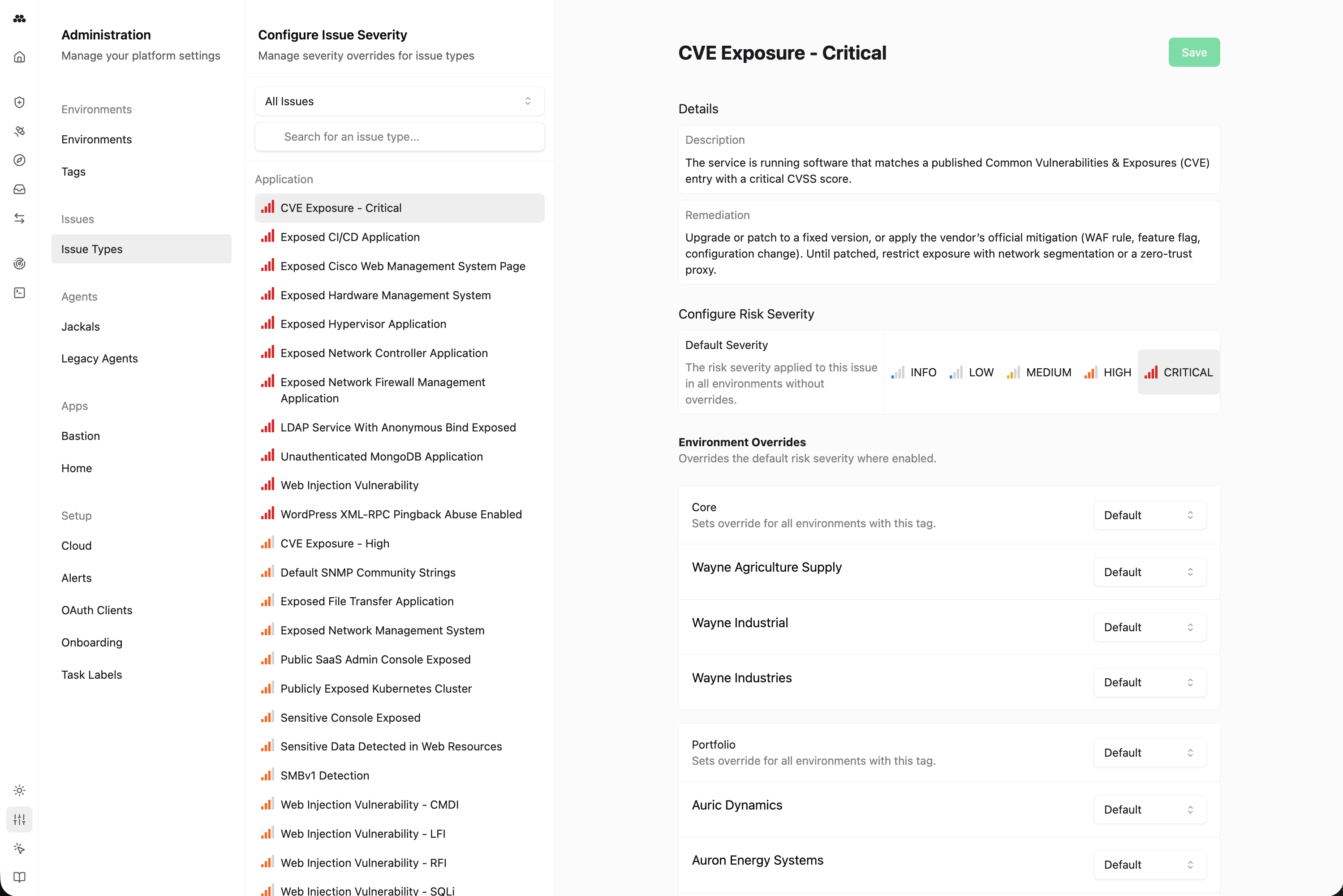
Risk Severities on Method Issues can now be adjusted, giving you more control over your Issue triage workflows. Every Issue in Method ships with a Method-suggested default severity. This can now be overriden for all environments or individual environments to match its significance within that environment.
Issues also see a number of smaller quality of life improvements:
- The Issues app now allows you to filter by First Seen and Last Seen dates for every Issue, so you can focus on current exposures and vulnerabilities.
- Issues now have richer titles showing more details of the underlying asset.
- Method’s API now includes the
Issue Remediationfield, allowing you to synchronize remediation steps to your external ticketing systems.
The following tools have been released or updated. You can view them in the Tools app and Operator app in Method.
- New: Kubernetes Console Exposure probes common Kubernetes API and health check paths to identify exposed Kubernetes services or misconfigurations.
- New: SMB Jackal Drop deploys a Jackal agent to a remote Windows host via SMB.
- New: SSH Jackal Drop deploys a Jackal agent to a remote host via SSH.
- Updated: Service Fingerprinting and Web Fingerprint now recognize a wide range of sensitive internal applications such as CI/CD platforms (Jenkins, TeamCity), network management systems (Barracuda Email Security Gateway, Cisco DCNM, Dell Sonic, F5 BIG-IP), Hypervisors (VMware ESXi, VMware Fusion, VMware vSphere), database systems (MySQL, PostgreSQL, MongoDB, Redis, Oracle, Microsoft SQL Server), and many more.
October 6, 2025
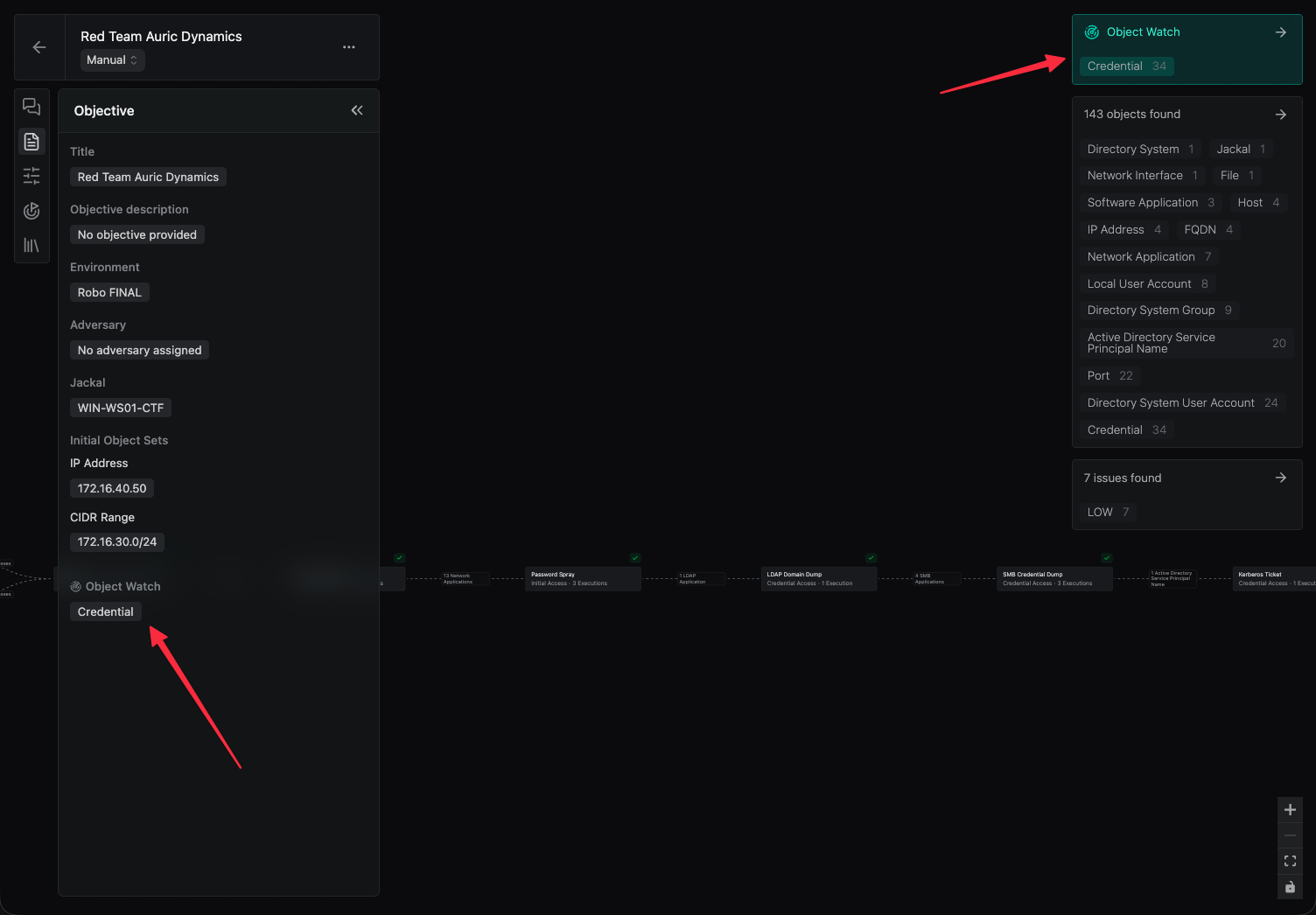
Operator can now watch for specific objects to help identify valuable assets within discovered data. During Operation setup, configure Object Watch to look for object types or object property values that align with the Operation’s objectives – for example, configure Operator to indicate when a Credential has been discovered.
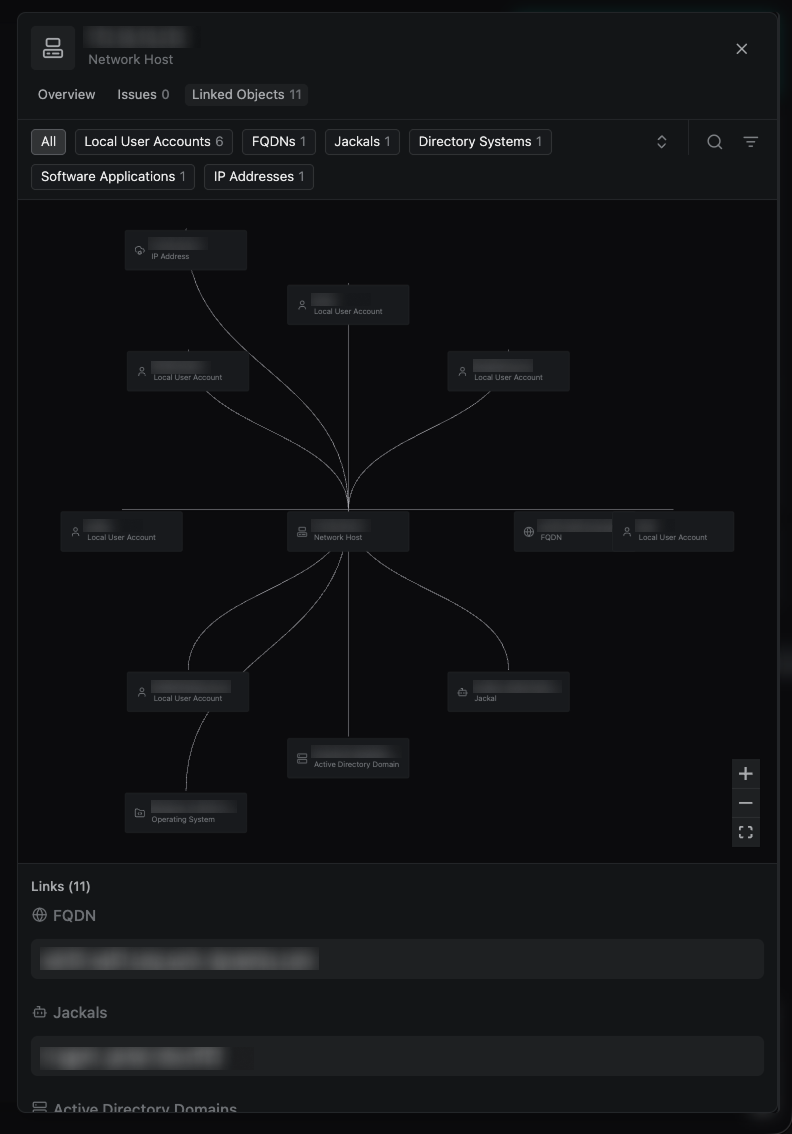
Operators can now visually explore linked Object discoveries using the graph view that shows related objects.
Method has an improved AWS integration to provide a comprehensive inventory of accounts, services, and resources. It covers all major AWS primitives, including identities, networks, and cloud assets, through safe, read-only API calls. With this foundation, users can leverage Method’s blackbox tools and now enumerate Cloud Objects to gain a deeper, end-to-end understanding of their cloud footprint.
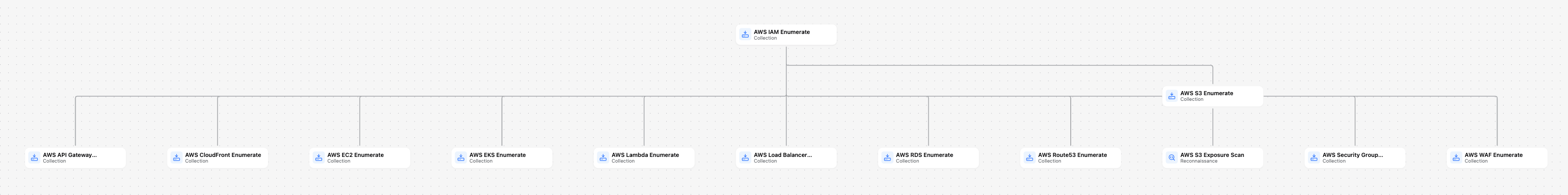
15 updated tools have been released. You can view them in the Tools app in Method.
- Updated: AWS API Gateway Enumerate enumerates all the API Gateway instances of an AWS account. This tool is useful for understanding the security rules, policies, and configurations of API Gateway instances in AWS.
- Updated: AWS CloudFront Enumerate enumerates all the CloudFront resources of an AWS account. This tool is useful for understanding the content delivery networks, distributions, and caching configurations of CloudFront in AWS.
- Updated: AWS EC2 Enumerate enumerates all the EC2 resources of an AWS account. This tool is useful for understanding the compute instances, volumes, and networking configurations of EC2 resources in AWS.
- Updated: AWS EKS Creds retrieves the credentials for an EKS cluster. This tool is useful for retrieving the credentials for an EKS cluster in AWS.
- Updated: AWS EKS Enumerate enumerates all the EKS clusters of an AWS account. This tool is useful for understanding the security rules, policies, and configurations of EKS clusters in AWS.
- Updated: AWS IAM Enumerate enumerates all the IAM resources of an AWS account. This tool is useful for understanding the security rules, policies, and configurations of IAM resources in AWS.
- Updated: AWS Lambda Enumerate enumerates all the Lambda functions of an AWS account. This tool is useful for understanding the security rules, policies, and configurations of WAF web ACLs in AWS.
- Updated: AWS Load Balancer Enumerate enumerates all the Load Balancer resources of an AWS account. This tool is useful for understanding the traffic distribution, health checks, and target group configurationsof Load Balancers in AWS.
- Updated: AWS RDS Enumerate enumerates all the RDS instances of an AWS account. This tool is useful for understanding the security rules, policies, and configurations of RDS instances in AWS.
- Updated: AWS Route53 Enumerate enumerates all the Route53 resources of an AWS account. This tool is useful for understanding the DNS configurations, hosted zones, and record sets of Route53 in AWS.
- Updated: AWS S3 Enumerate enumerates all the S3 resources of an AWS account. This tool is useful for understanding the storage, permissions, and metadata of S3 buckets in AWS.
- Updated: AWS S3 Exposure Scan scans and analyzes public-facing S3 buckets without credentials to determine existence, access controls, directory listings, and anonymous read capabilities. Includes support for parsing various S3 URL formats and inspecting policies and ACLs for potential misconfigurations.
- Updated: AWS Security Group Enumerate enumerates all the Security Groups of an AWS account. This tool is useful for understanding the security rules, policies, and configurations of Security Groups in AWS.
- Updated: AWS VPC Enumerate enumerates all the VPCs of an AWS account. This tool is useful for understanding the security rules, policies, and configurations of VPCs in AWS.
- Updated: AWS WAF Enumerate enumerates all the WAF resources of an AWS account. This tool is useful for understanding the security rules, policies, and configurations of WAF web ACLs in AWS.
September 22, 2025
Available in beta: Sync Issues from Method to your preferred ticketing system using Method’s webhooks integration and SDK.
- Use Method to set up powerful security automations, then track, assign, and close issues in your favorite project management tool.
- Easily hop back in to Method to explore assets linked to your issues in Explorer and run operations against them in Operator.
We’ll be expanding the API and SDK over the coming months based on early usage and feedback. Reach out to your Method contact to schedule getting started.
Two new or improved tools have been released. You can view them in the Tools app in Method and try them in Operator.
- New: Kerberos Service Ticket exploits resource-based constrained delegation (RBCD), constrained delation, and unconstrained delegation to request service tickets for arbitrary service principle name (SPN) as any domain user enabling service-impersonation based lateral movement and privilege escalation.
- New: DCSync emulates a domain controller via MSRPC to pull the domain operating context, allowing full credential exfiltration and permanent domain persistence.
September 8, 2025
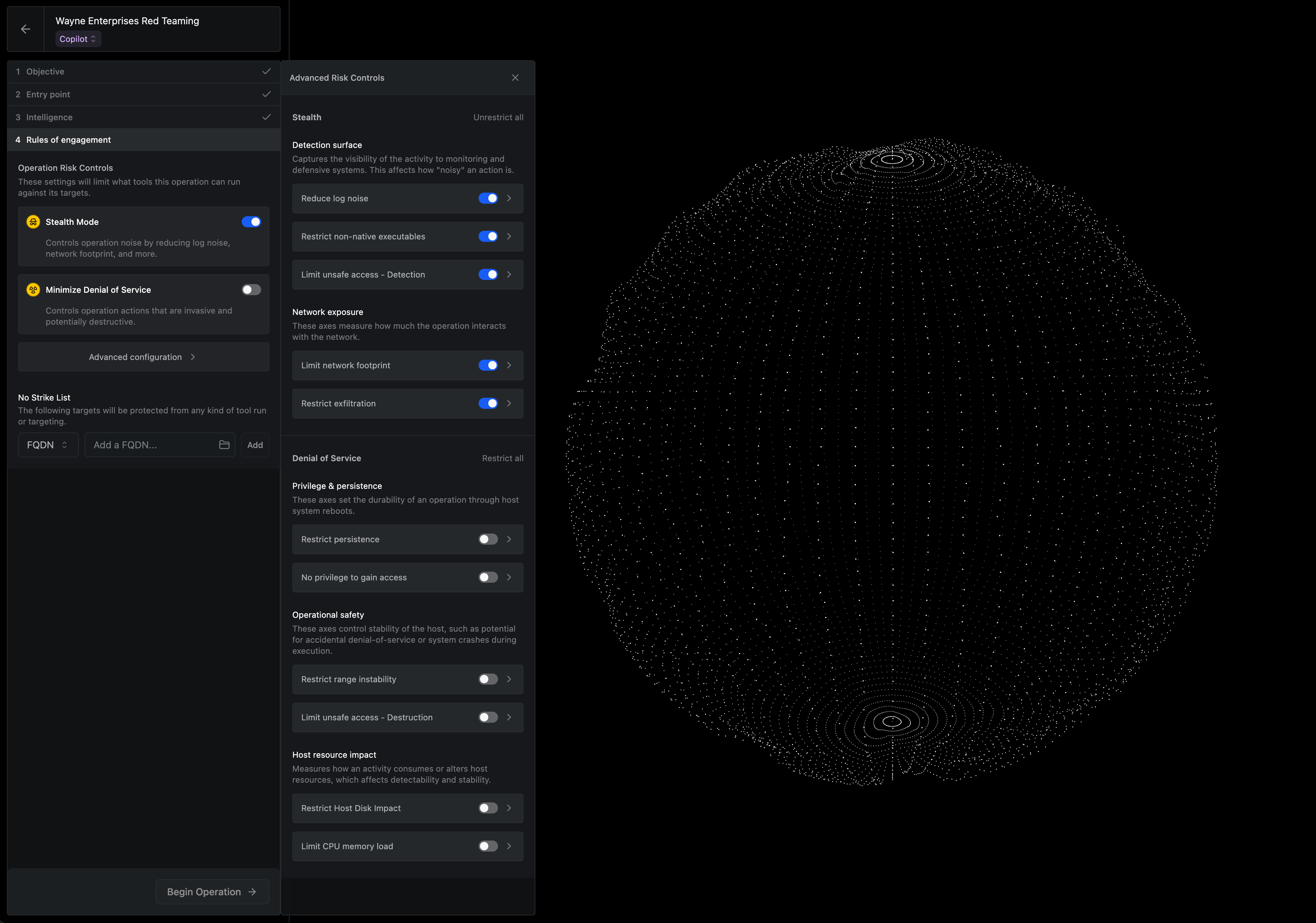
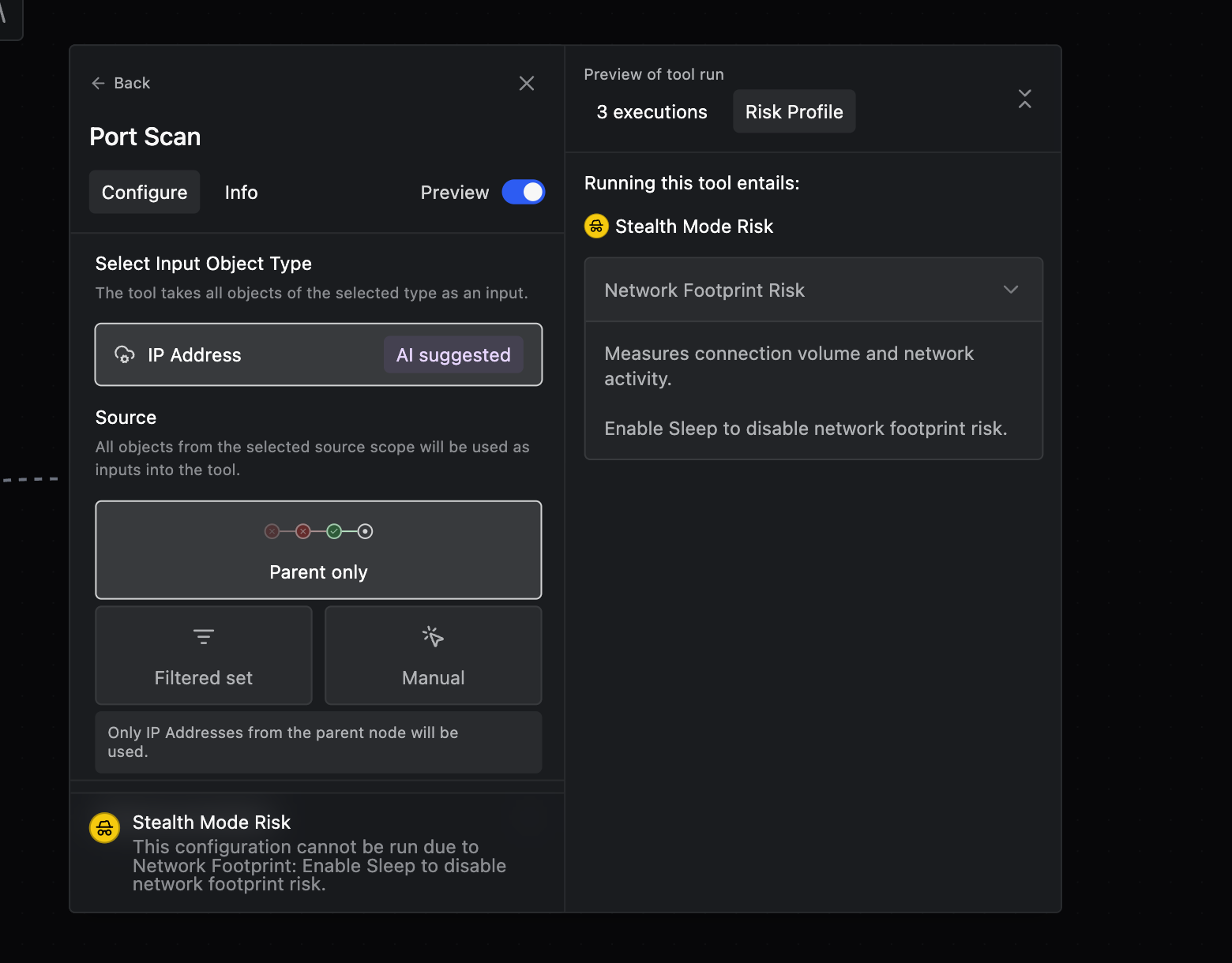
Operators can now configure specific risk axes to minimize their risk of detection within a specific Operation. Choose from 11 risk axes that give you granular control over facets such as log noise, network footprint, exfiltration, and more. See the full list in Operator during setup.
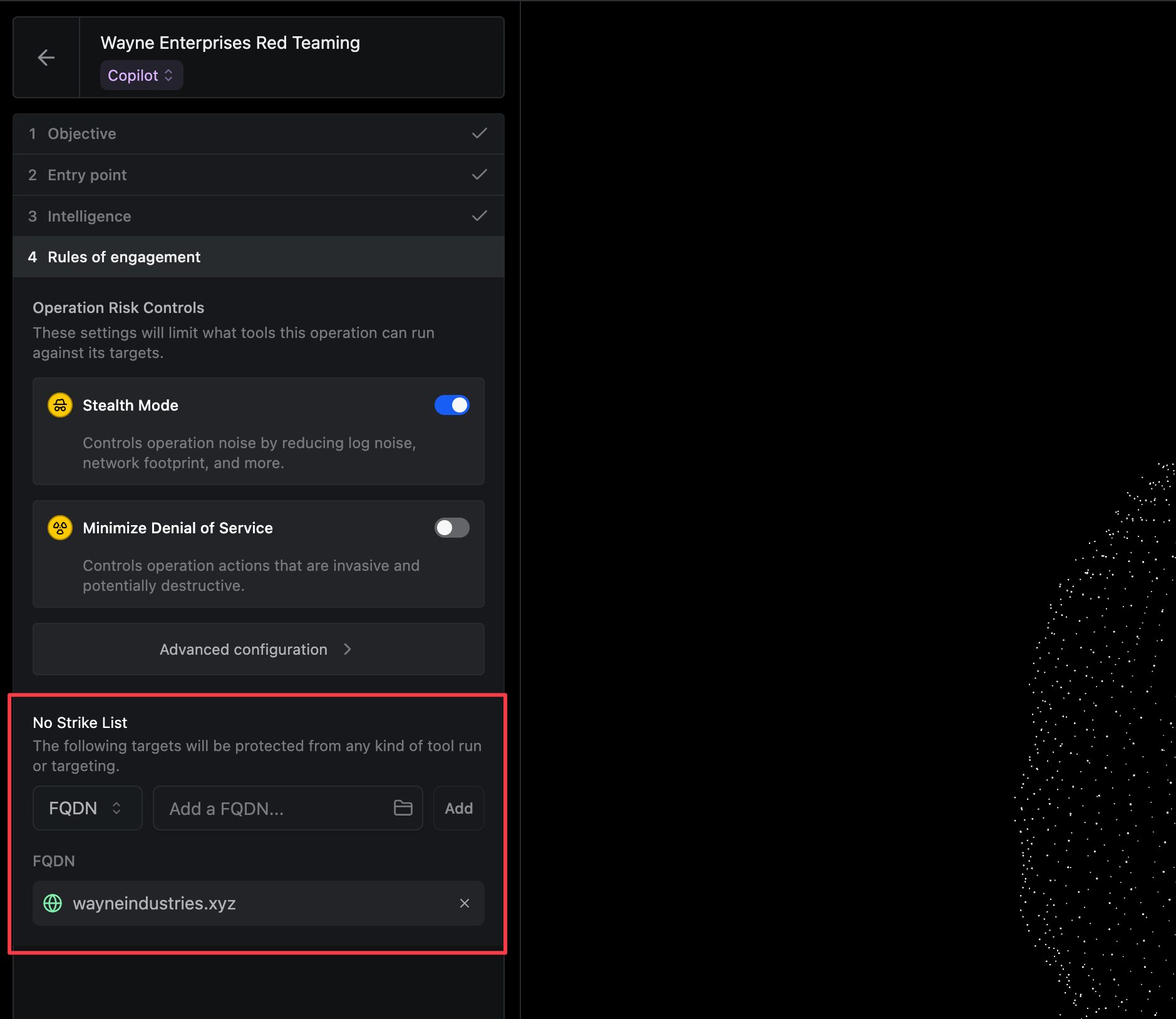
Operators can now set certain targets as No Strike, which restricts tool runs against specific, off-limits targets for the duration of the Operation.
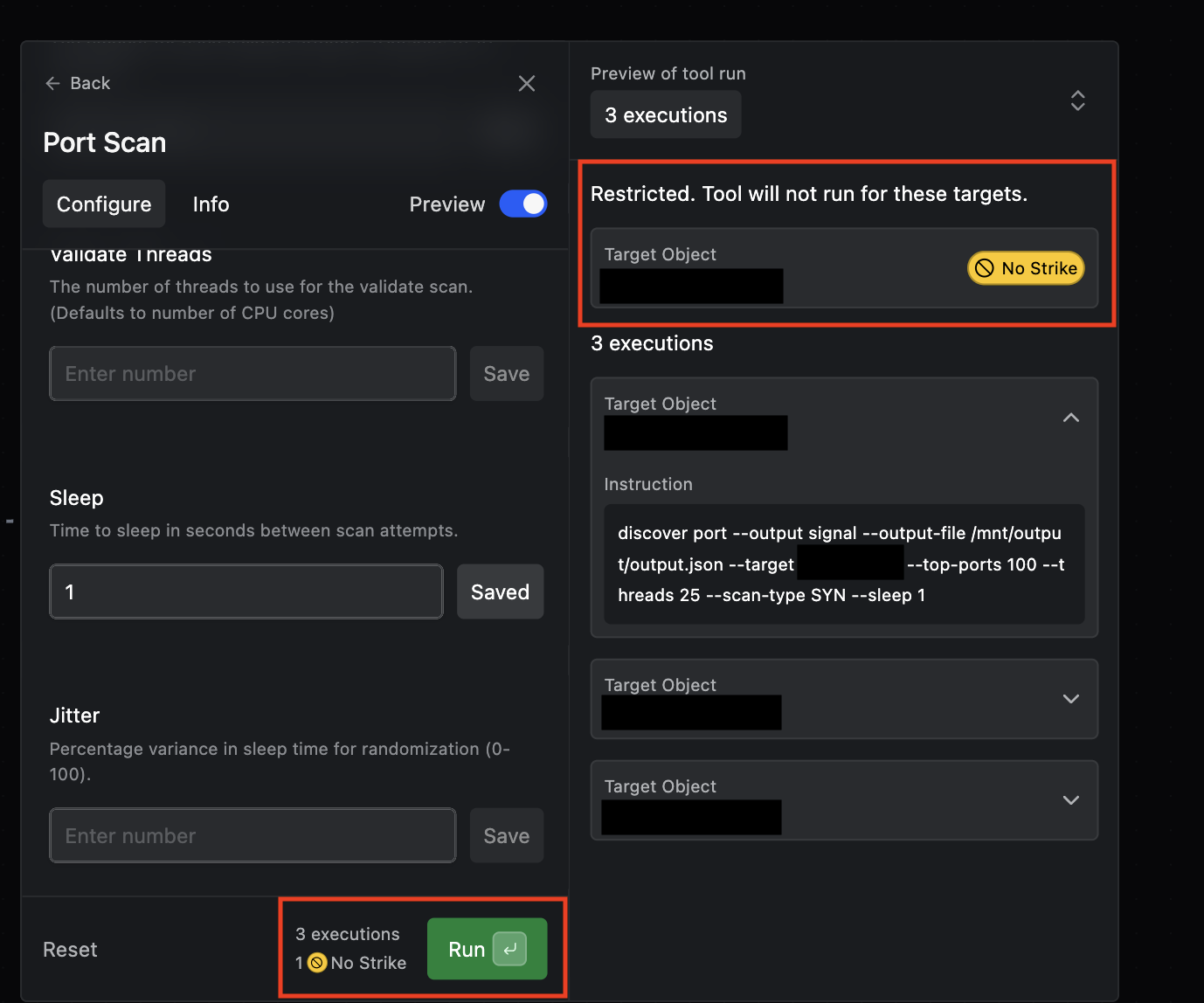
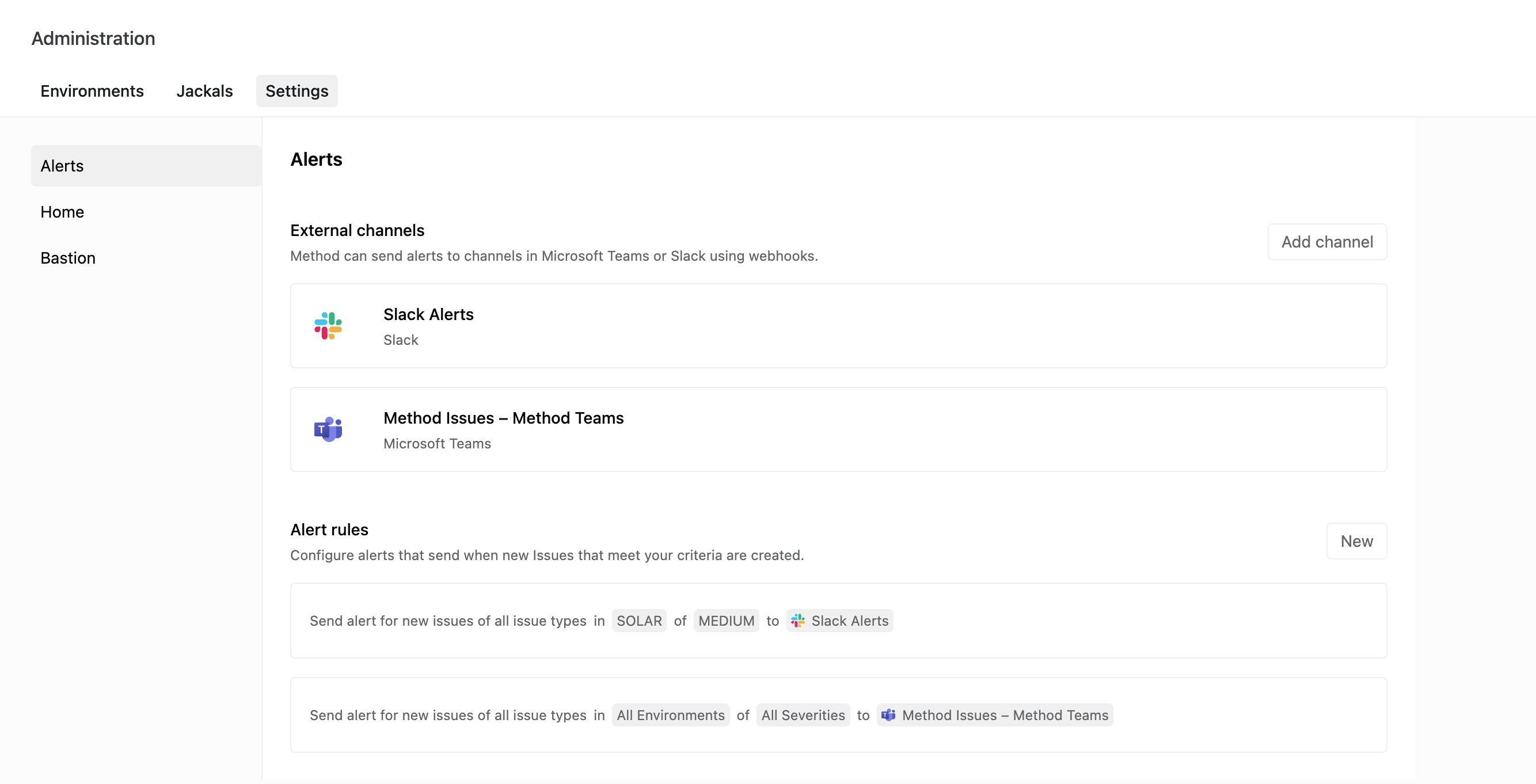
Method can now send you alerts in Slack or Microsoft Teams when new Issues are discovered. You can create rules that trigger alerts that meet any of following criteria: environment, issue type, and issue severity.
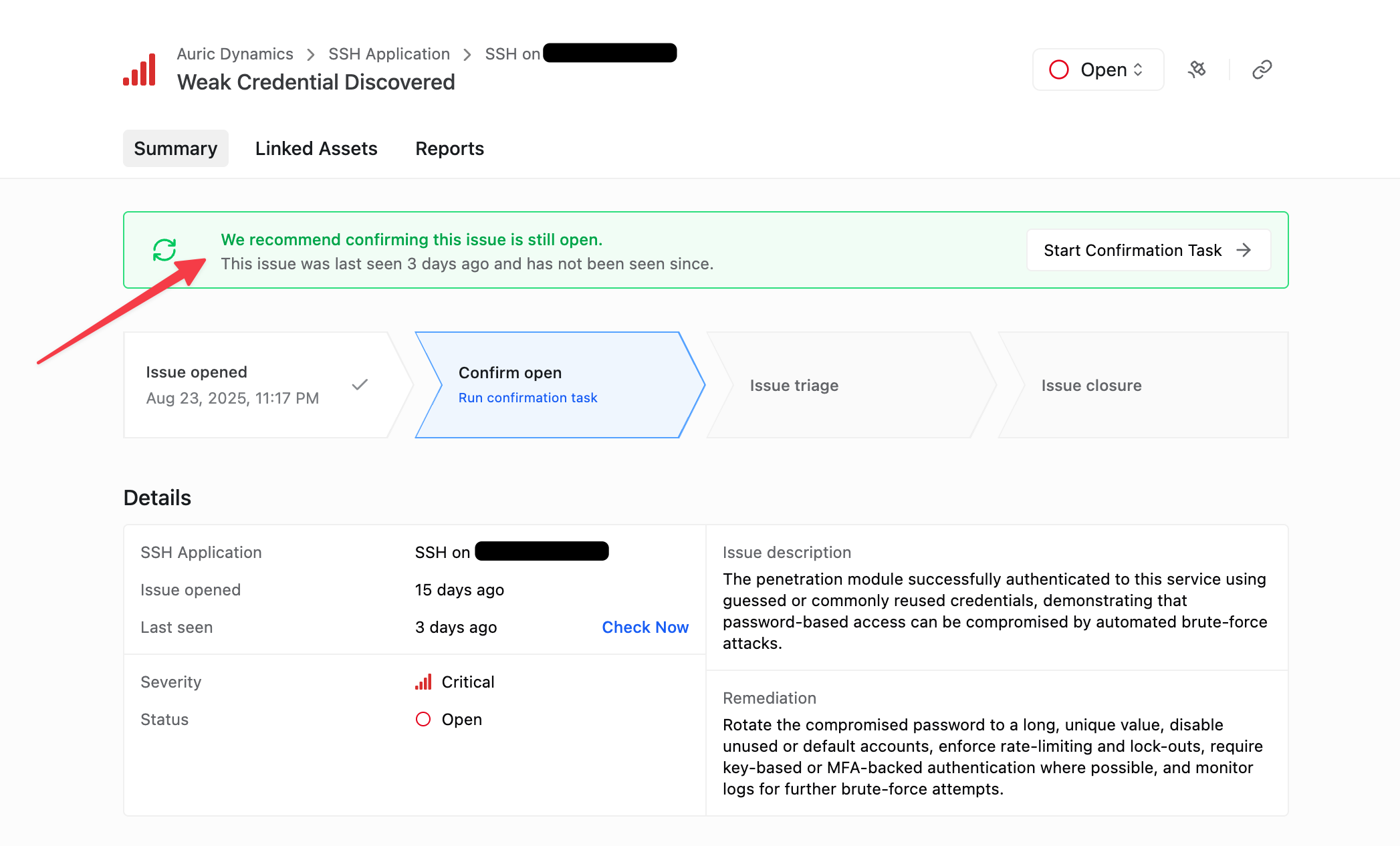
You can now re-scan for an Issue with one click to see if it is still open. The Issue View will tell you when the issue was last seen. If the Issue hasn’t been seen in the last 24 hours, you will be reminded to check for it again.
August 25, 2025
Method’s data exploration has been overhauled with a fluid new experience. Environments, Issues, and Objects open in stacking panels that allow you to quickly navigate from one asset to the next. You can now traverse different paths through your system without switching tabs or losing your place.
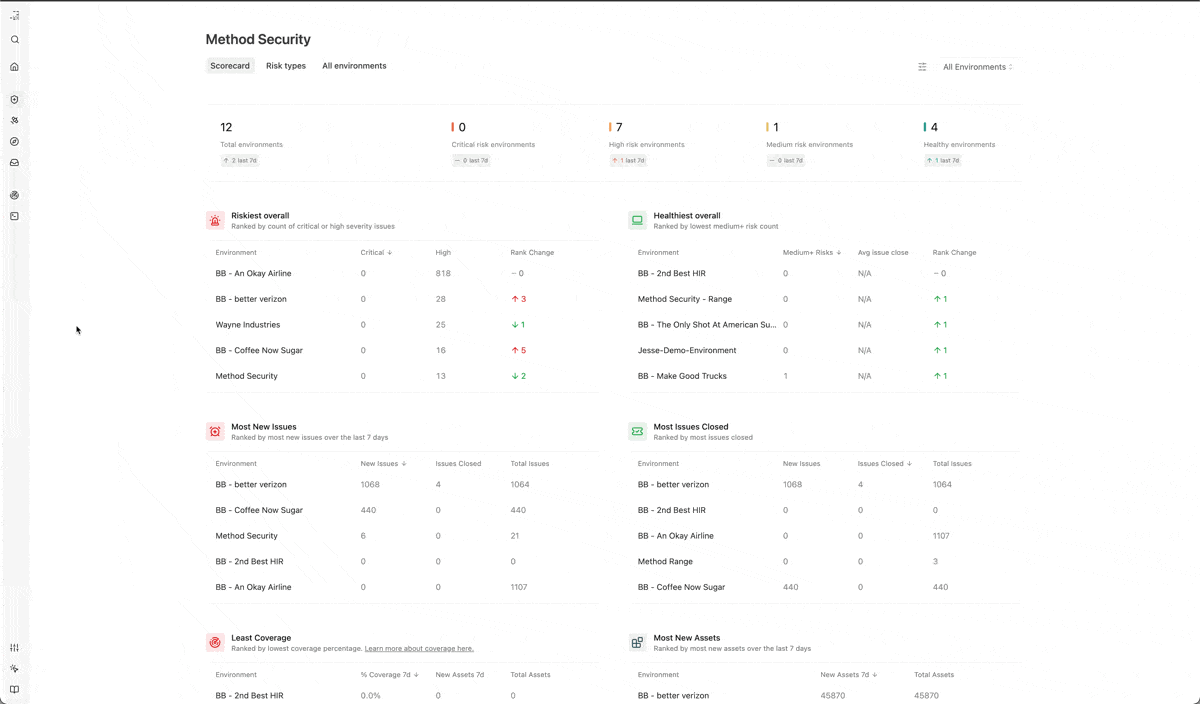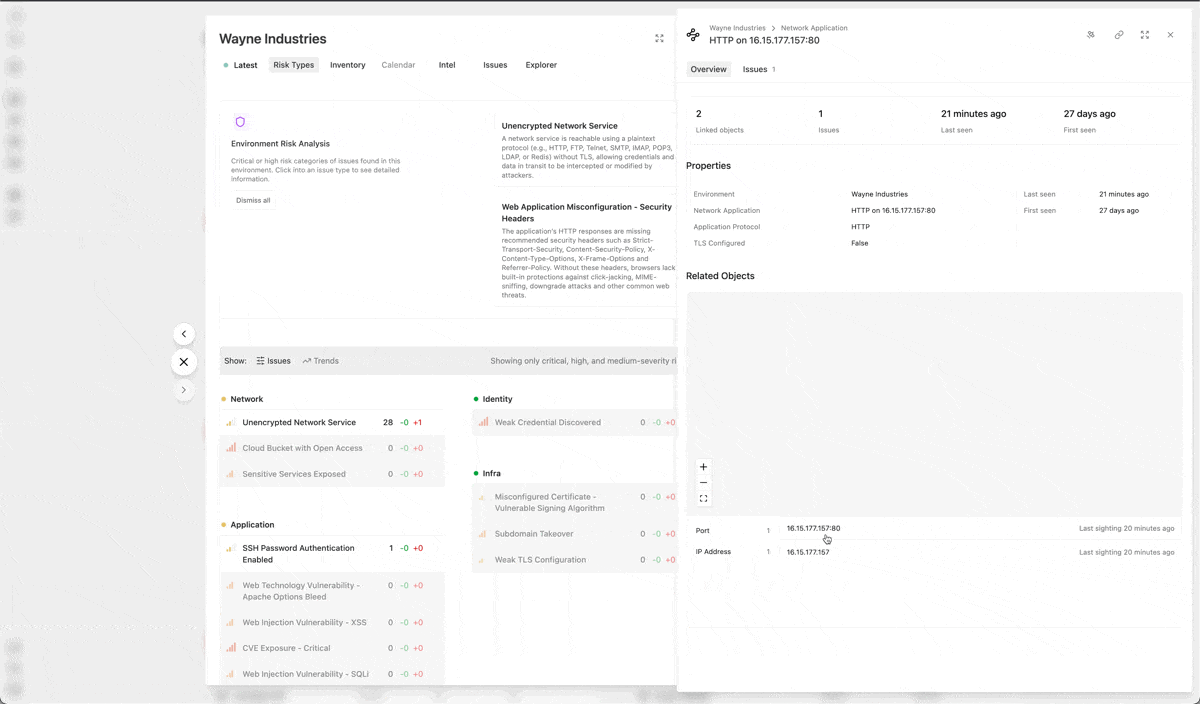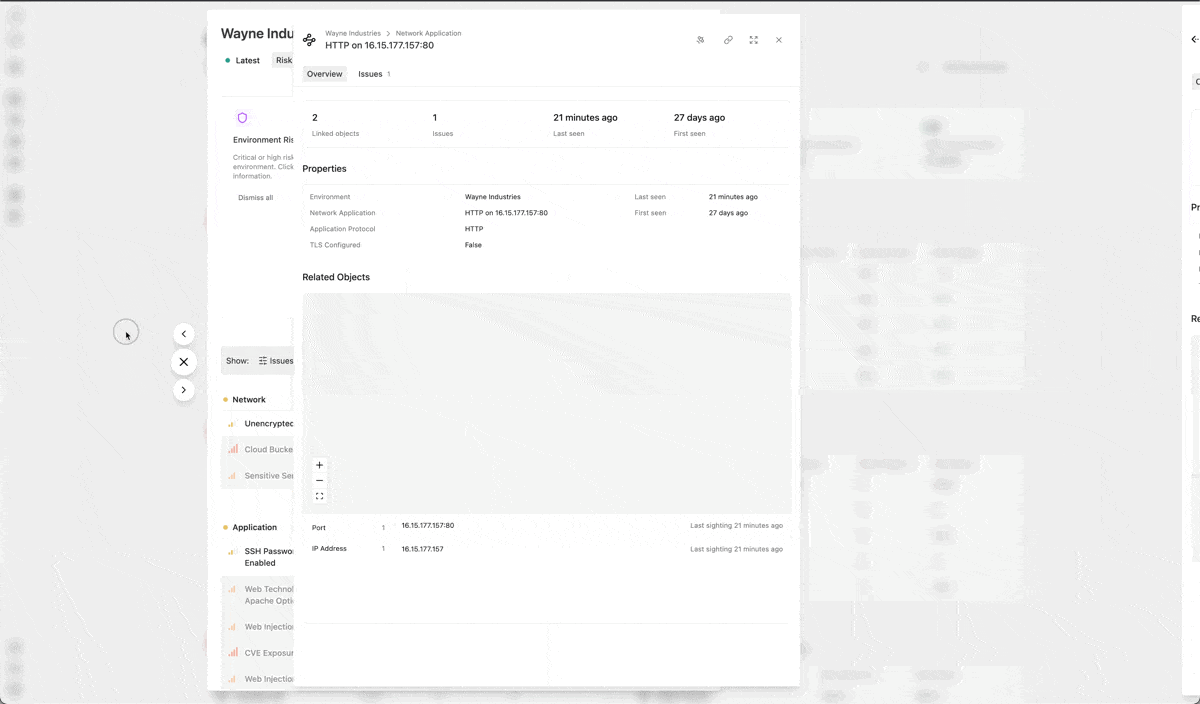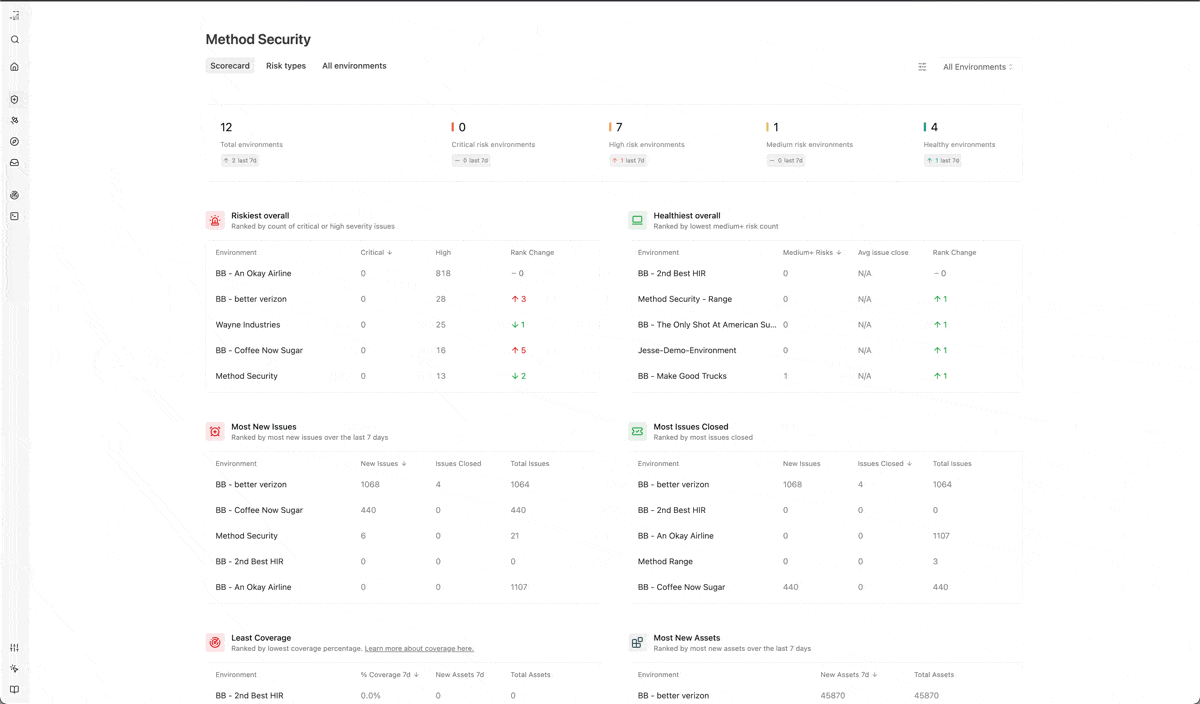
Operator’s data exploration has also been revamped, using the same new experience paired with powerful, new capabilities, including: keyword search, flexible filters, and better data presentation to make it easier to see and understand what you’ve found in your operation.
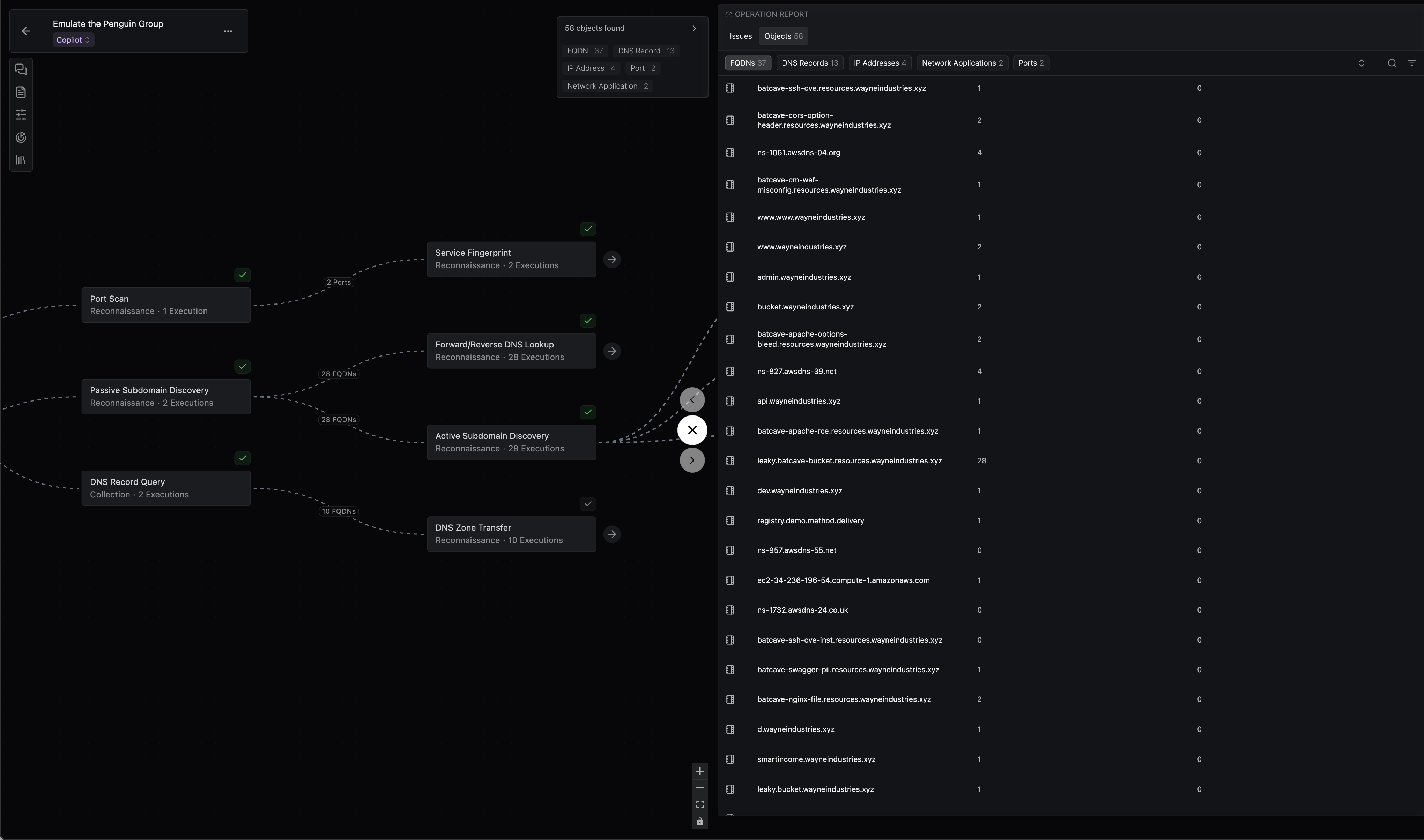
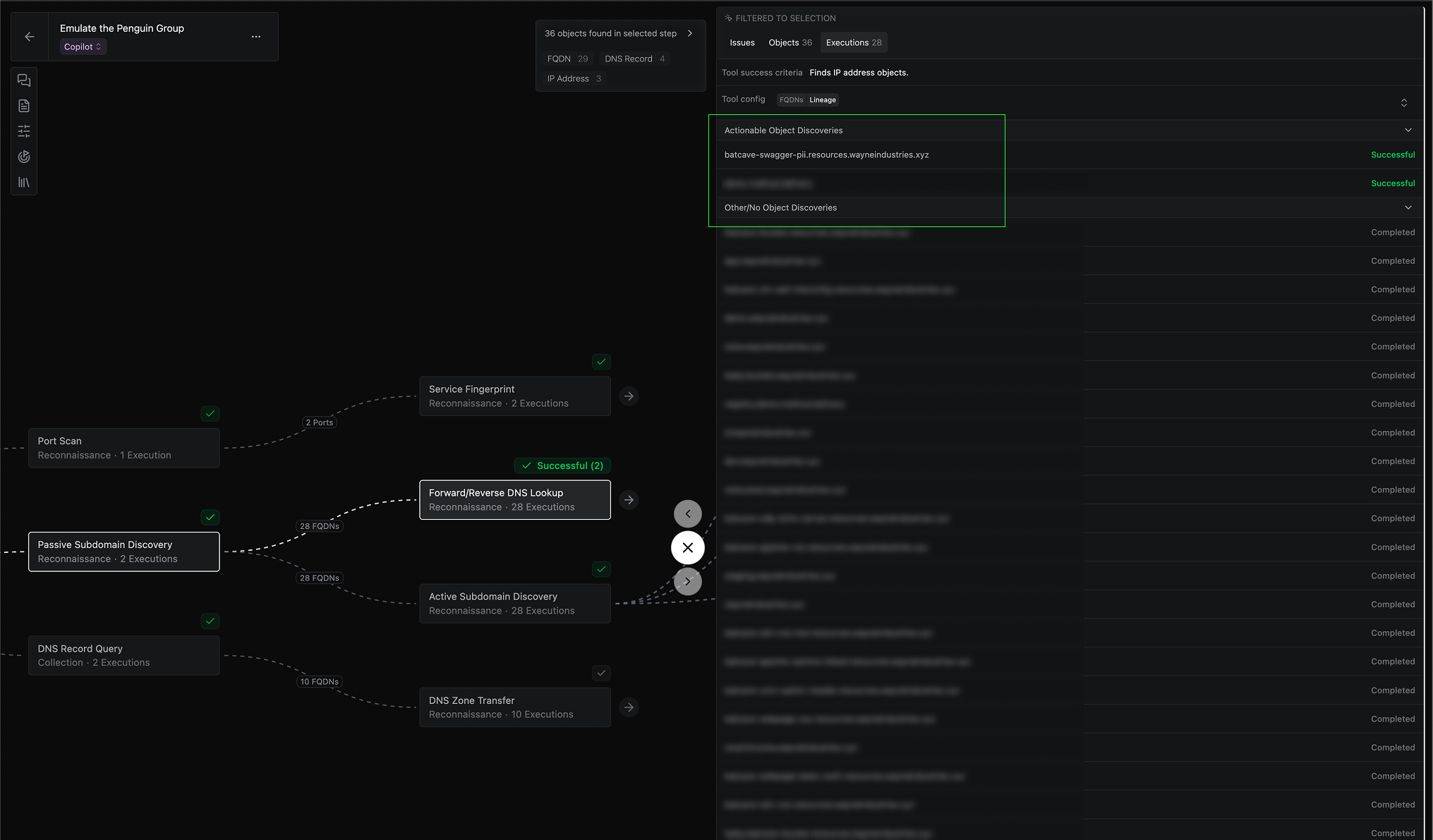
Operations now show whether discovered assets are actionable. Tool runs that find actionable data objects will now be distinguished from those that completed without finding actionable data. These changes make it easier to decide which branches in your operation are useful and actionable and which are not.
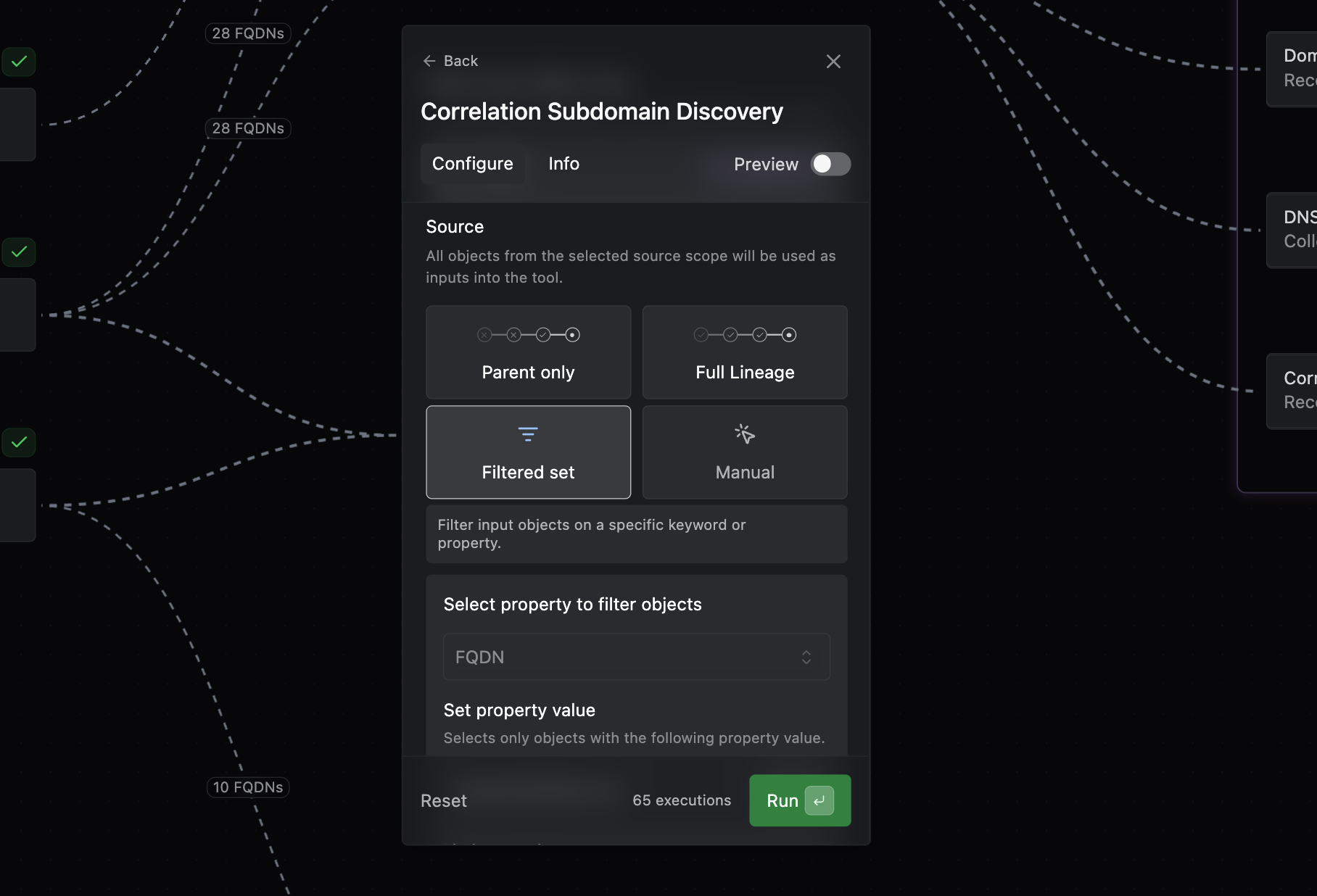
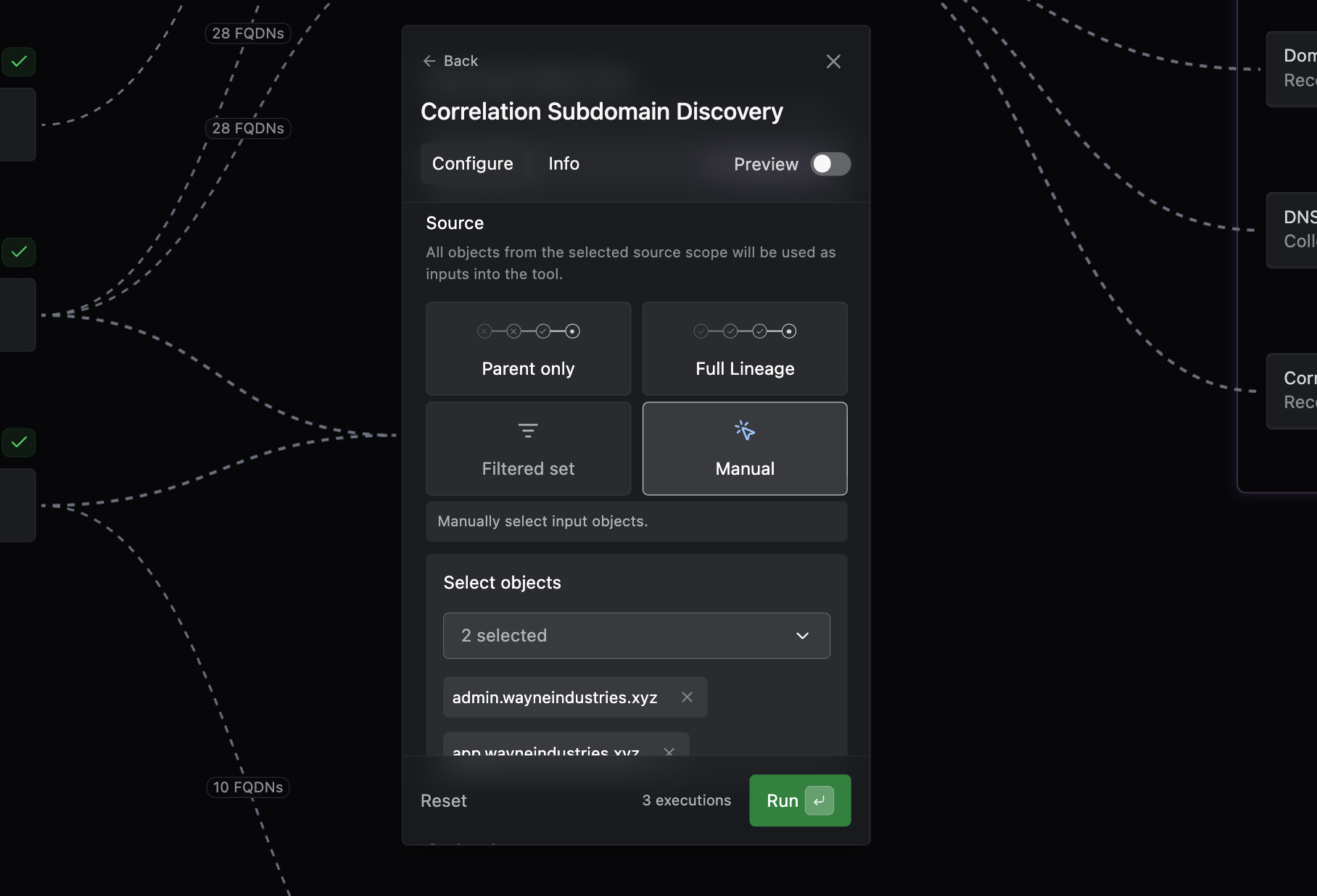
Operator tools now support granular selection of input objects. You can now select targets for your tool runs more precisely using filters or manual selection.
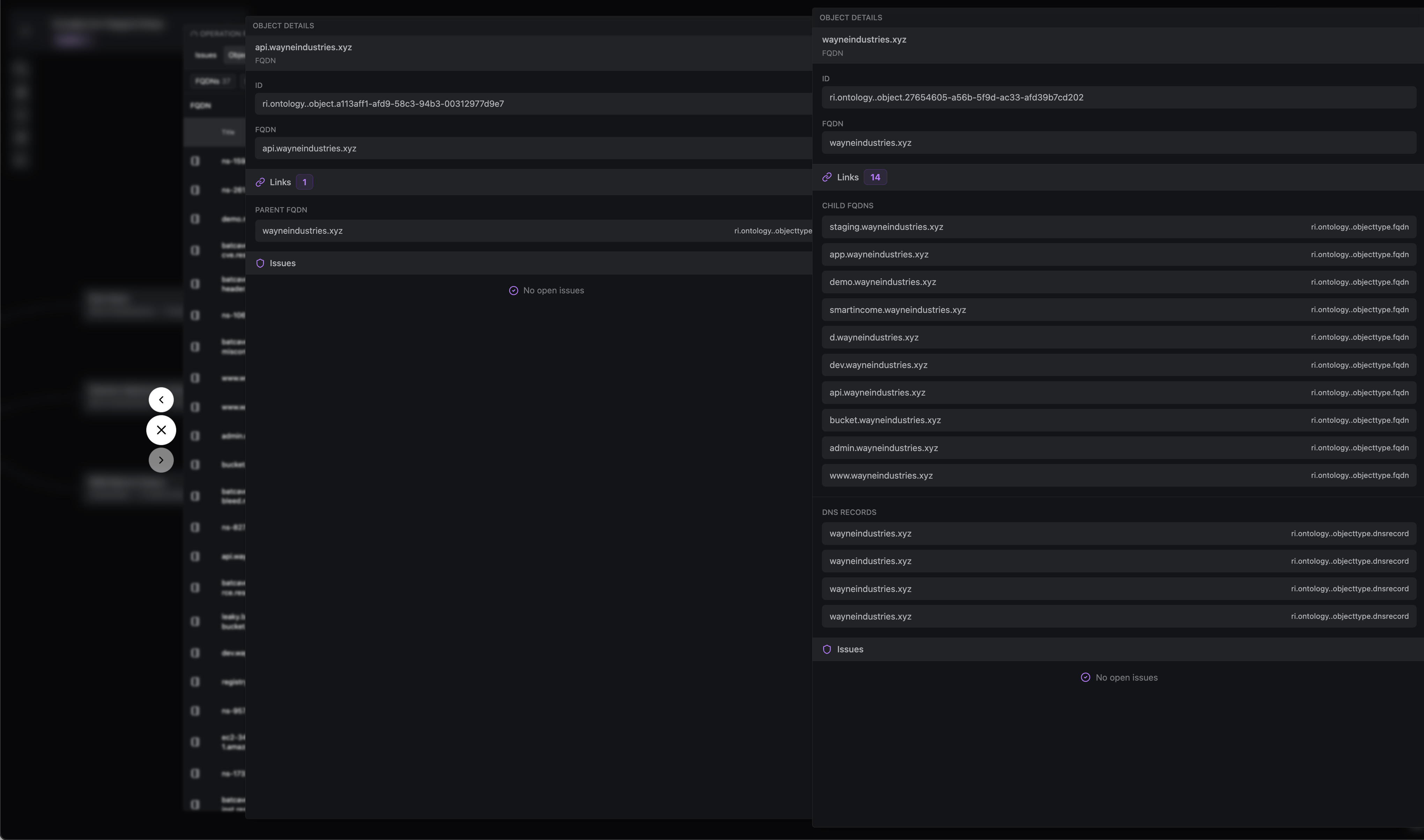
Easily see related objects on Issue and Object views with the Related Objects graph on Issues and Objects.
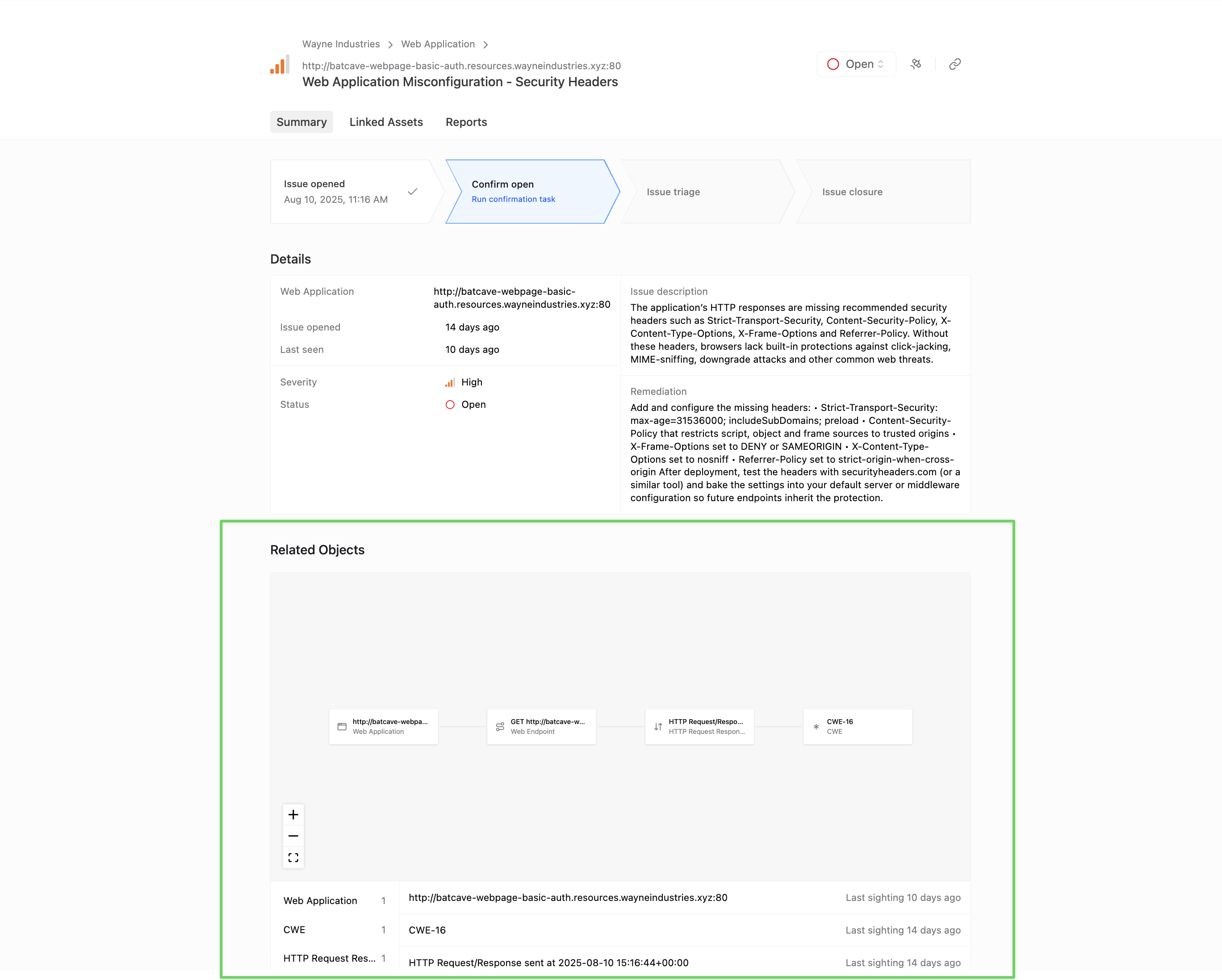
Four new or improved tools have been released. You can view them in the Tools app in Method and try them in Operator.
- New: Host Discovery Tool performs ping scans against CIDRs / IP addresses. Supports several scan types.
- New: SMB Shares Enumeration enumerates SMB shares for access permissions.
- New: Web Page Static Asset Takeover Detection identifies stale or unclaimed static assets that are loaded on a user’s webpage that may be vulnerable to takeover.
- Improved: Internal Network Pentest and Internal Network Discovery now feature stealth modes to support red team workflows.
August 4, 2025
Issues have been re-imagined from the ground-up with more powerful capabilities and a new design. You can now track Issues by status and perform your issue investigation without leaving the Issue view. Coming soon: viewing the history of an issue and leaving comments.
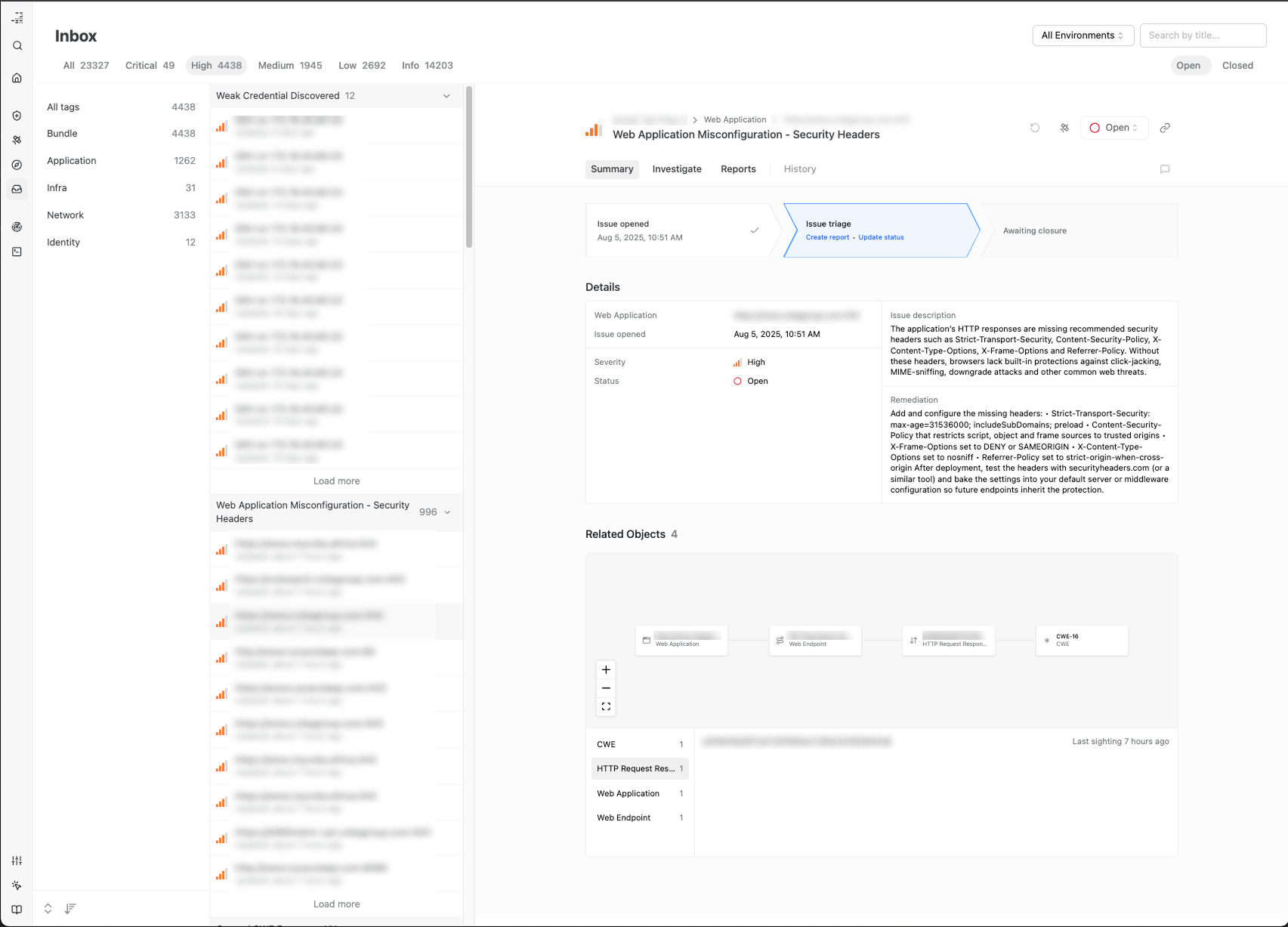
You can now auto-generate Issue Reports to share with colleagues who do not have Method access. Issue Reports allow you to share details of the issue such as severity, date discovered, issue description, remediation, and the details of the assets associated with the issue. Coming soon: instructions for the Report recipient to reproduce the issue without needing access to Method.

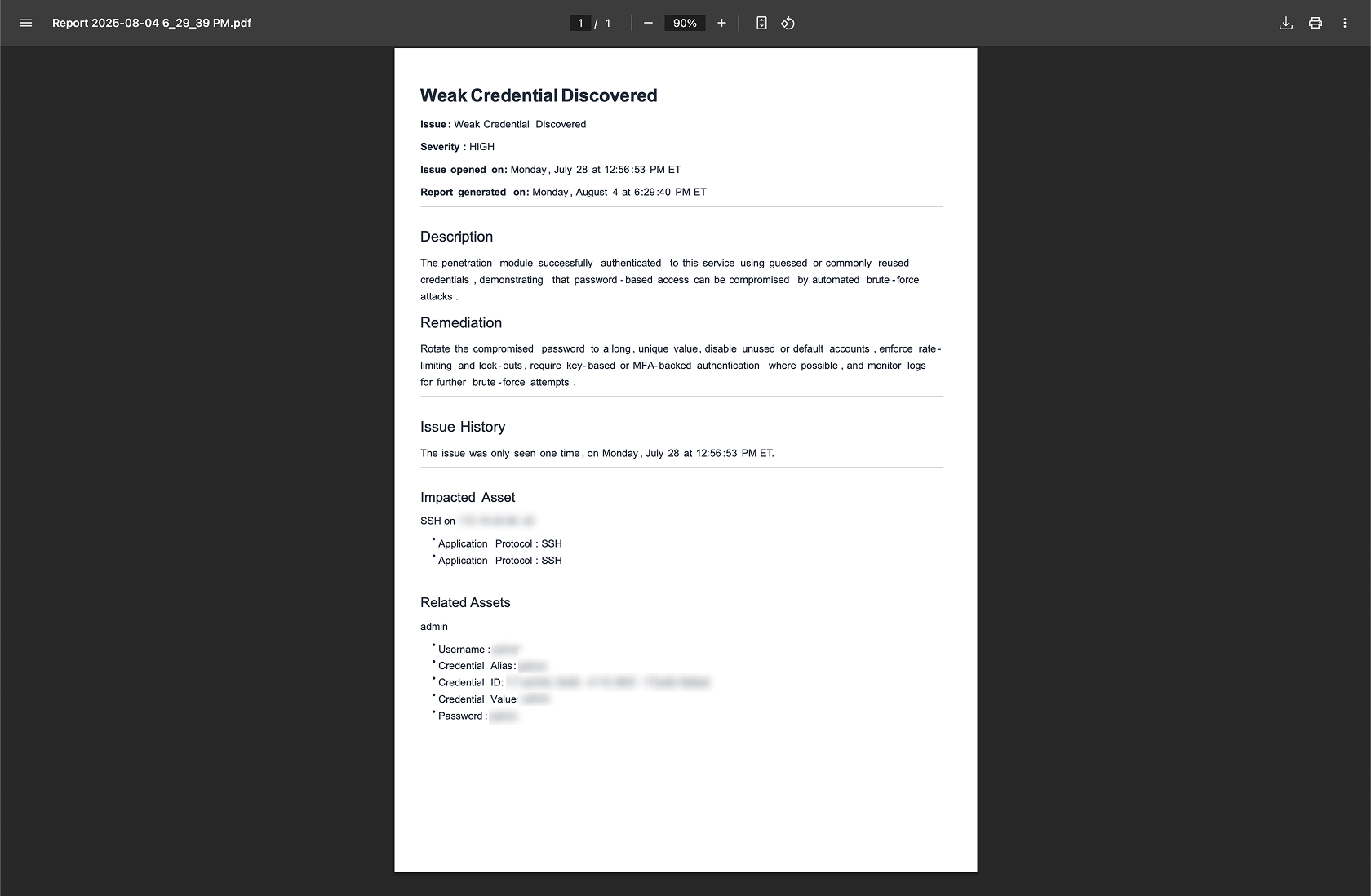
Five new tools have been released. You can view them in the Tools app in Method and try them in Operator.
- New: Domain Discover identifies active domains from network applications or IP addresses on on-premise networks.
- New: Username Spray attempts to enumerate valid usernames before spraying passwords against them.
- New: Password Spray attempts login using a single password on multiple usernames against non-HTTP services to gain initial access.
- New: LDAP Domain Dump enumerates users, groups, and relationships from Active Directory using LDAP domain enumeration.
- New: SMB Credential Dump uses valid admin credentials to access system security databases on Windows systems and extract password hashes and secrets.
July 21, 2025
Five new or improved tools have been released. You can view them in the Tools app in Method.
- New: Web CVE Scan scans web applications to identify known vulnerabilities from the last 25 years of CVEs.
- New: Web Technology Scan identifies known vulnerabilities in specific types of web servers.
- New: Web Misconfiguration Scan identifies misconfiguration in web applications. (Currently limited to headers with expansion coming soon.)
- Improved: Web WAF (Web Application Firewall) Detect detects which WAF is protecting web applications and web endpoints. Now has significantly better accuracy.
- Improved: Web DAST (Dynamic Application Security Testing) has been improved with expanded injection types, allowing you to detect more classes of exploitable vulnerabilities than before.
July 7, 2025
Bastion 2.0 is released. Use Bastion to evaluate your cross-environment defenses and to drill-down into any risk across your environments. Use the Scorecard tab to see your healthiest, riskiest, and most active environments. Use Risk Types to explore risk patterns that cross-environments. Drill down into any environment to see the specifics of its issues and assets.
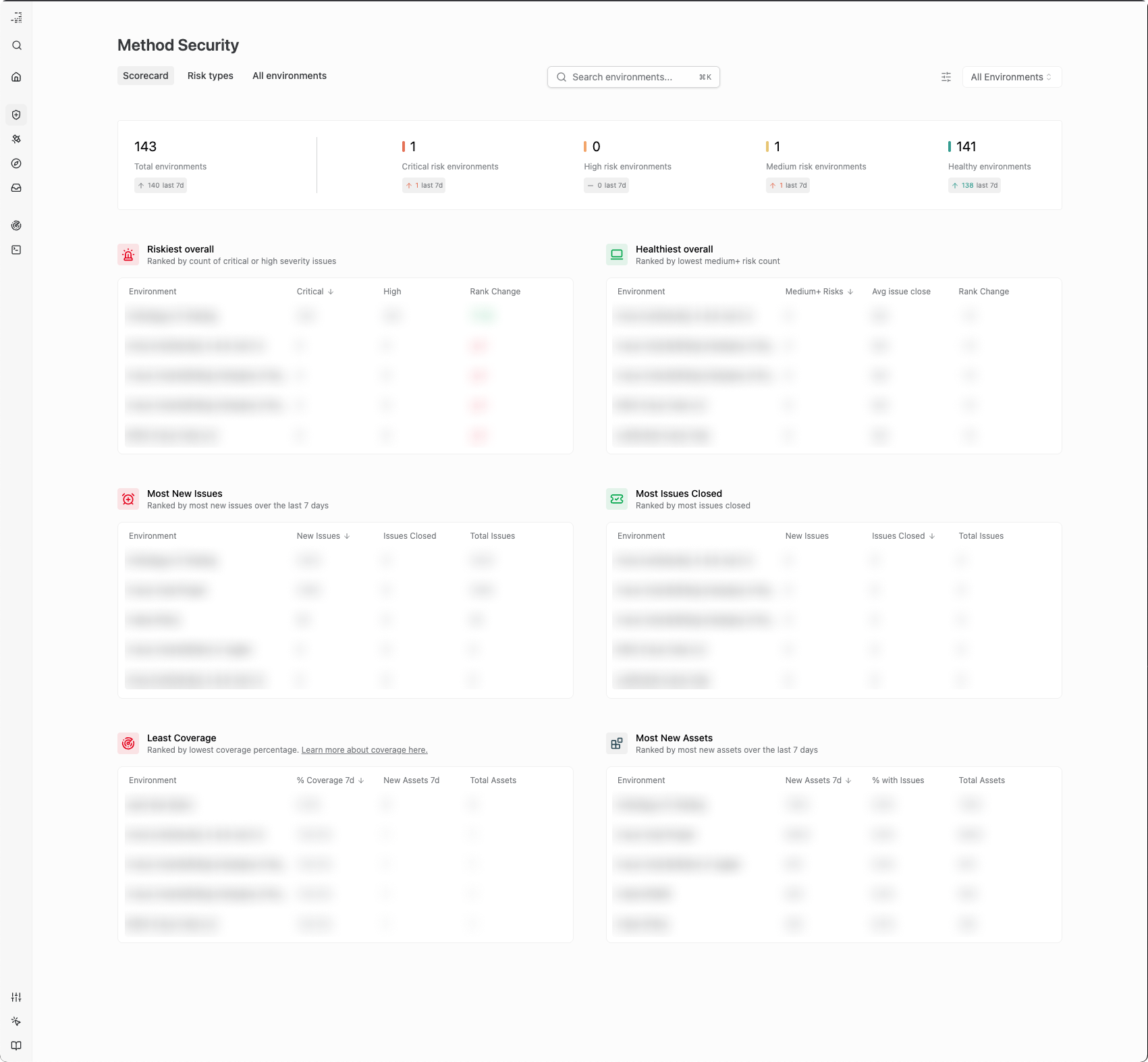
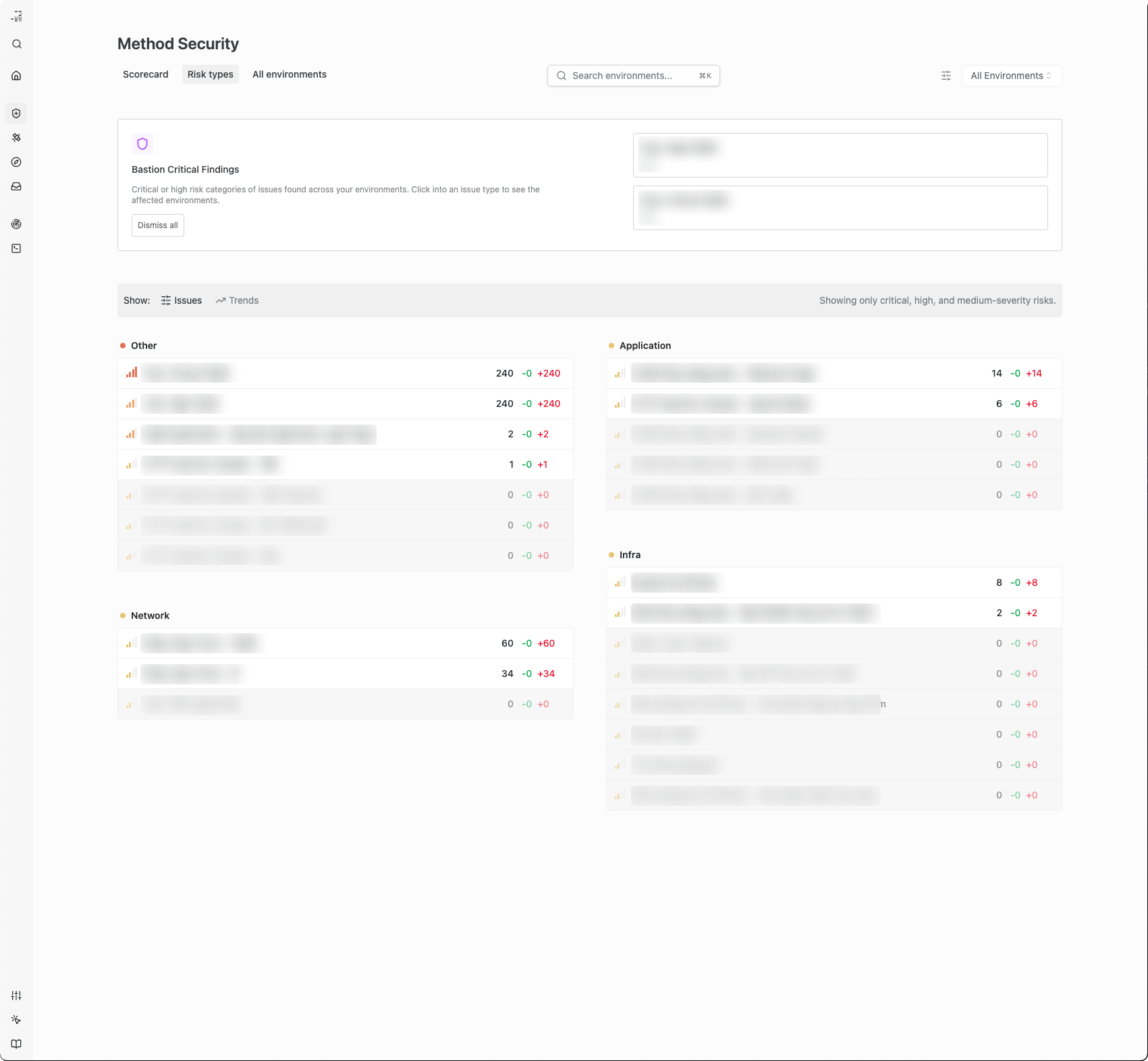
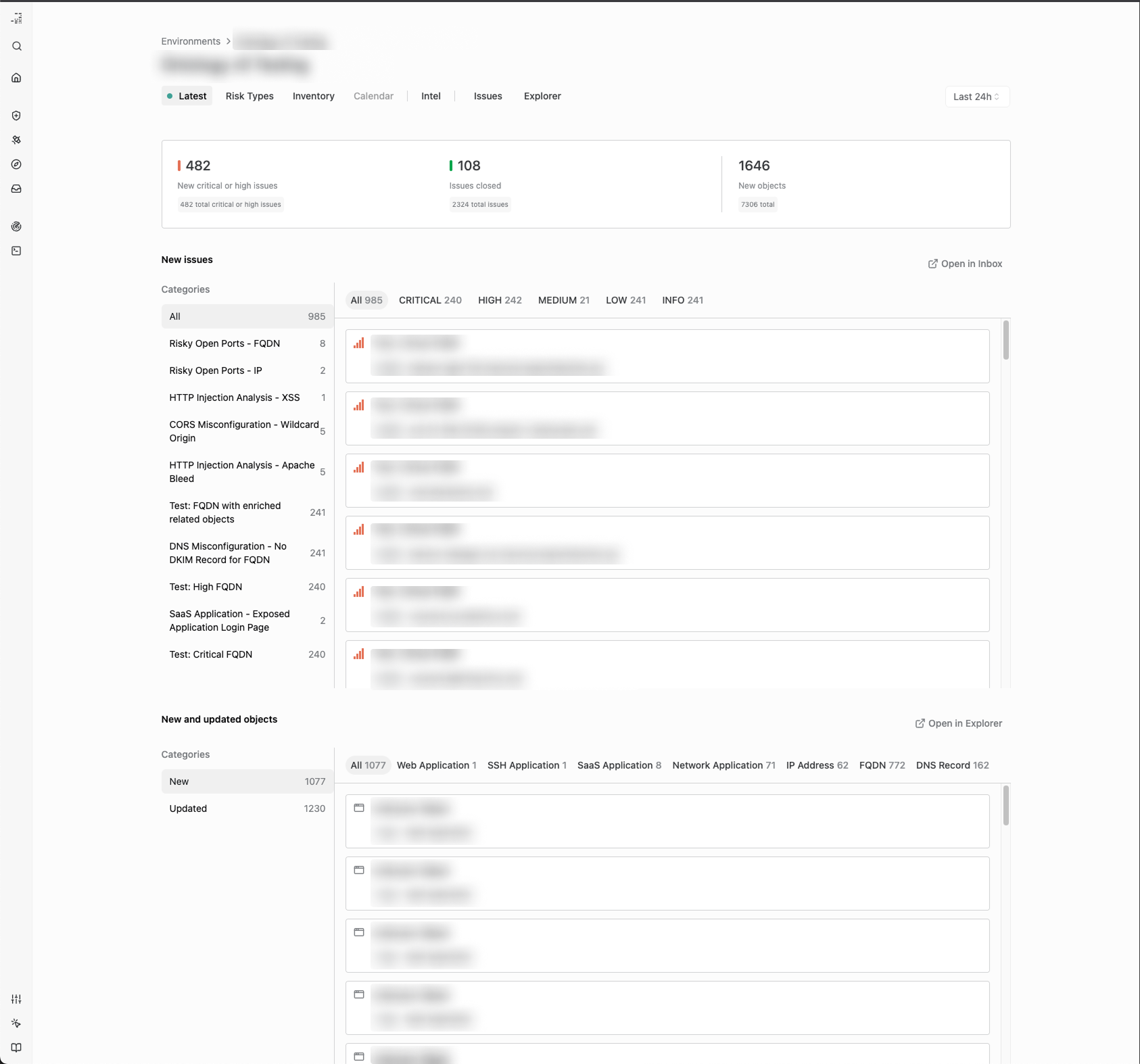
Environment views have been expanded and refreshed. You can now explore the Latest issues and New assets, risk patterns across the assets, track inventory in the environment, and more.
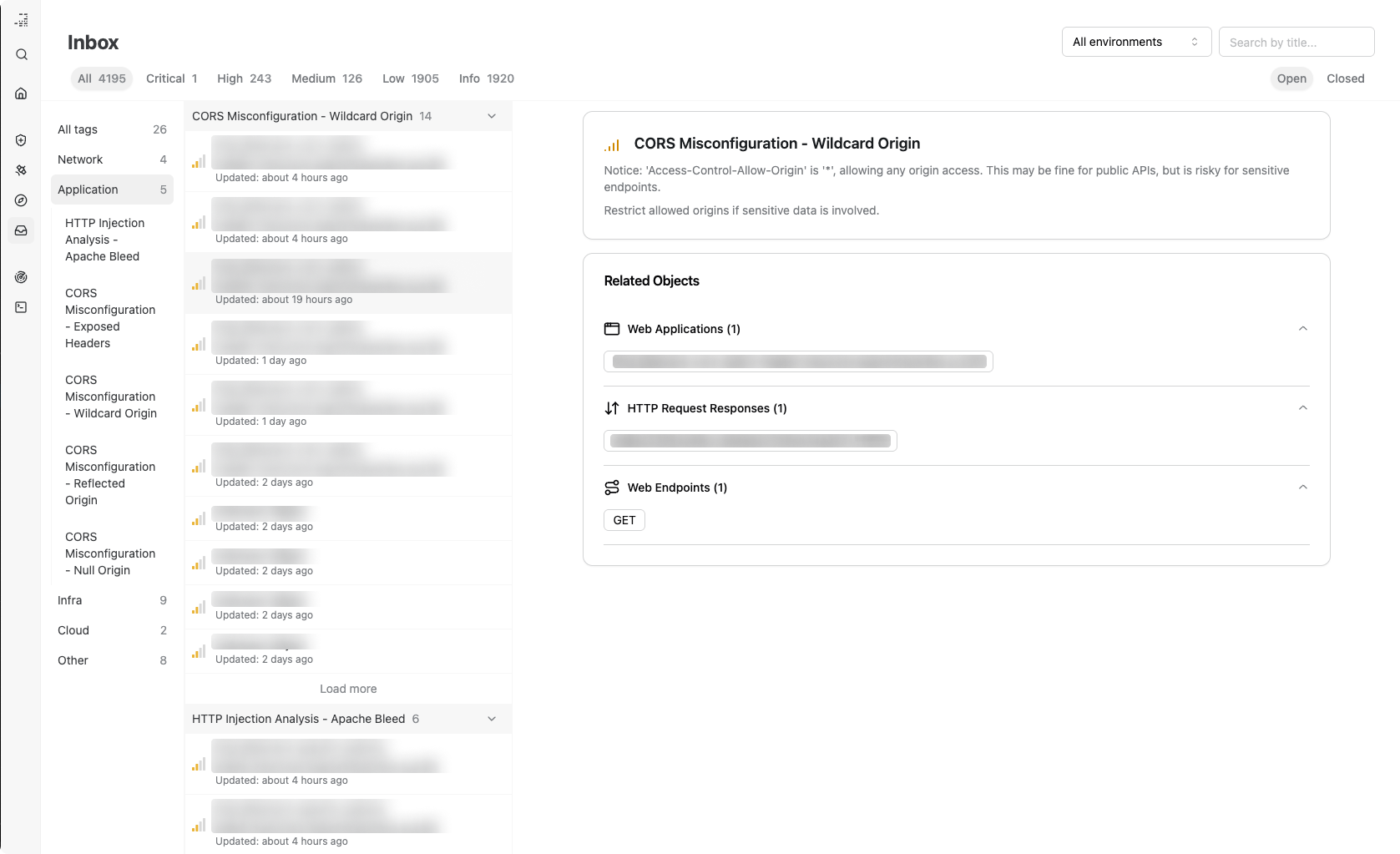
The Issue Inbox now supports better filtering. Explore issues by issue severity, issue tag, and environment.
Method Documentation now includes Guides. Guides are short tutorials to make you maximally effective when using Method. The first set of guides covers Bastion, Reaper, Explorer, Inbox, and Automator. Check them out here.
June 23, 2025
Tool selection and configuration in Operator is smarter and easier to use. Only tools that are available for use (with valid inputs available) appear as options. The tool configuration form is redesigned, with better explanations and labels. Use the Preview panel to preview the executions before they run.
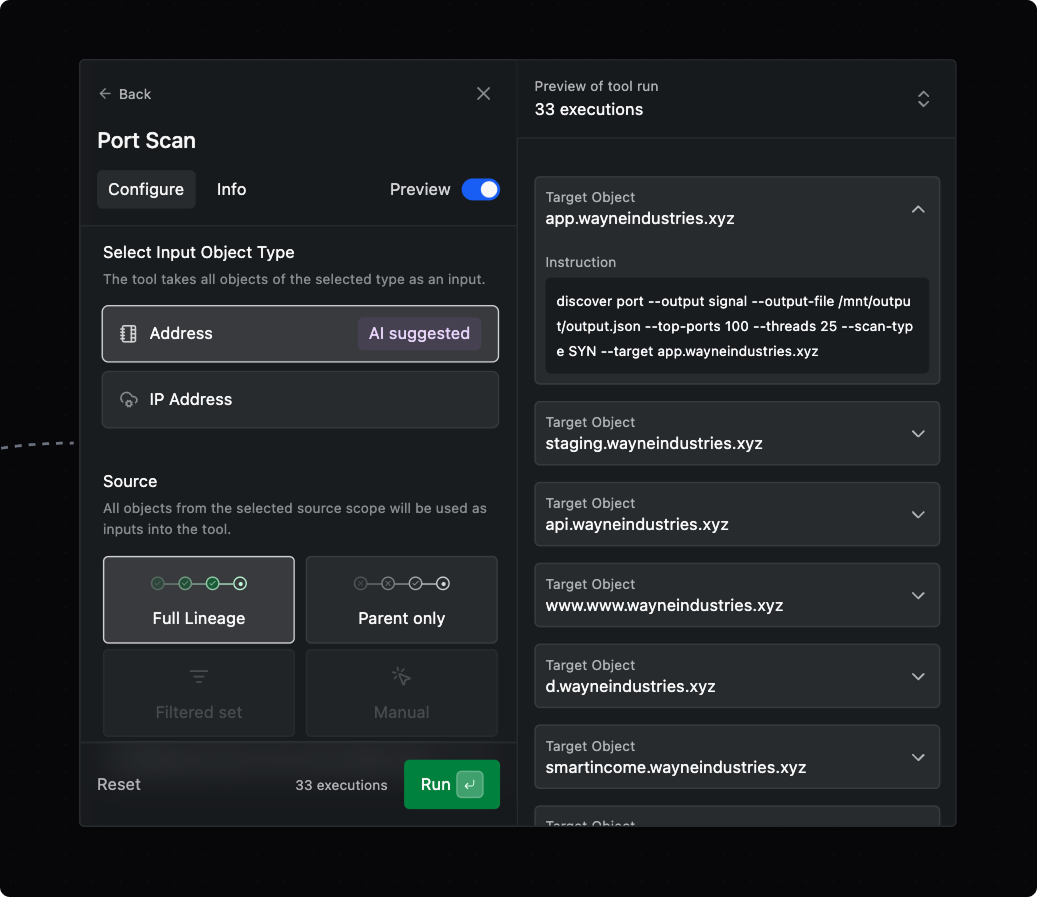
Operator’s AI Copilot has even deeper knowledge of Operation context and general security understanding.
Method has a new Homepage. Follow high-level metrics, kick off a search, and easily hop into any application.
Activity, Test Cases, and Tasks have a new home in the Automator app. Automator is the one-stop shop for all automations in the platform.
June 9, 2025
Reaper now supports Adversary Emulation. Create an Adversary in the Reaper app, then run adversary emulation operations in Operator. The Operator AI will use Adversary details to build its attack plan.