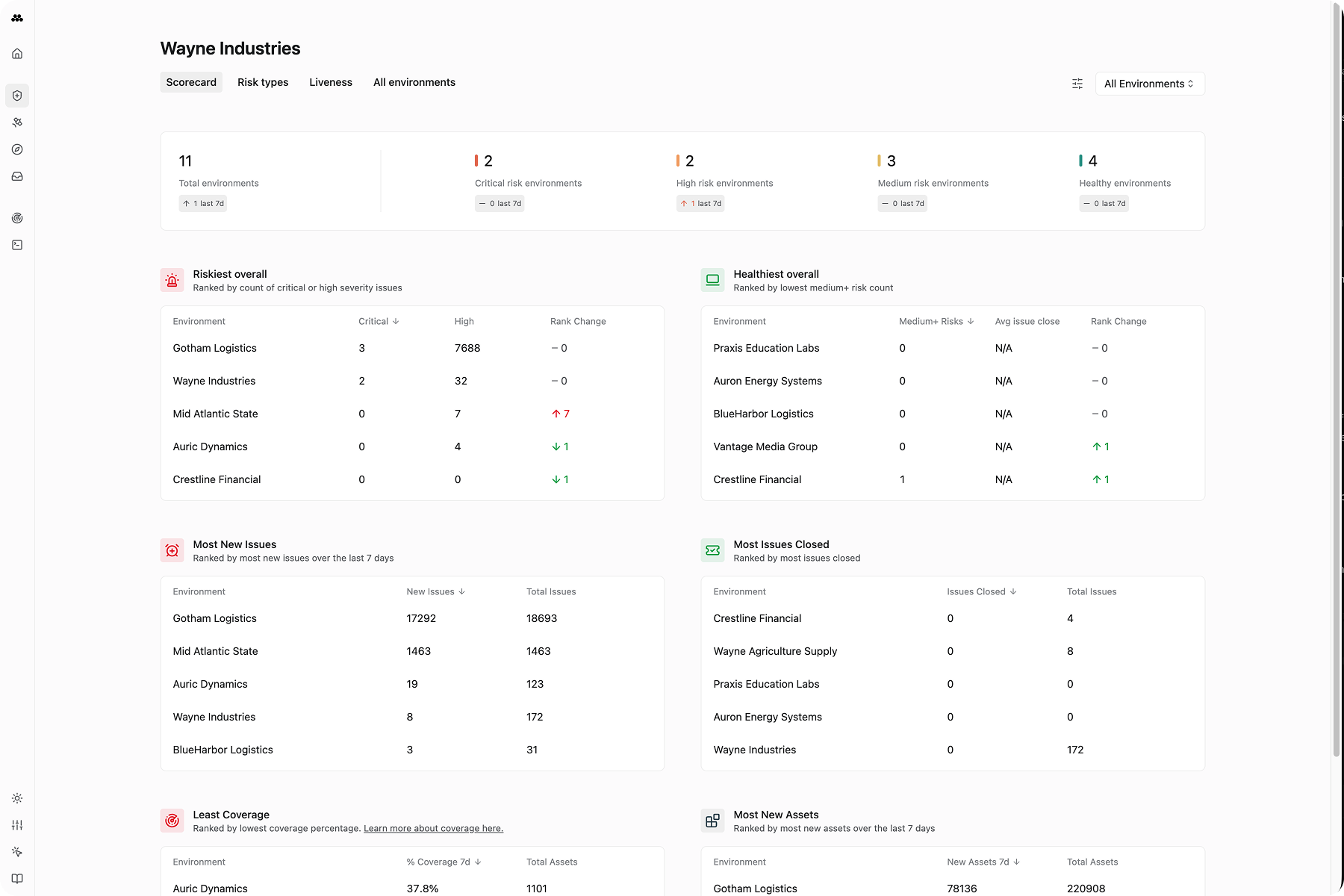
What is Method?
The Method Platform is a full spectrum security platform, spanning defensive and offensive capabilities, designed for all domains - cloud, on-premise, edge, apps, identity, endpoint, and more.
Accelerate the scale and speed of your security program through a continuous combination of defense and offense
The Method Platform is a full spectrum security platform combining autonomy, data, tooling, and command & control (C2) to power defensive and offensive products.
It is architected around two point of views regarding the future of security:
- In order to win, teams must safely harness autonomy at scale
- The most valuable outcomes are naturally cross-category, cross-domain, and cross-workflow
In essence, the Method Platform is the ultimate infrastructure for proactive security agents optimized for any environment. The platform is organized around two Products that capture large and distinct areas of security:
- Bastion - Digital-twin driven exposure management
- Map, validate, and control the totality of resources and possible attack paths in the context of your business
- Reaper - Software-defined offensive operations
- Plan and execute red team operations and adversary emulation exercises on top of robust autonomy and software defined C2 infrastructure
How is Method different?
The Method Platform is a new kind of security platform built to be more integrated, cross-domain, and AI-enabled than existing point solutions.
Built on a Data Ledger and Ontology
Almost every security workflow hits data roadblocks in the form of not connecting the dots across controls, environments, and organizational context. Method Platform is built on a Ledger which tracks security data temporally as well as by source. This Ledger feeds an Ontology, or security Digital Twin, consisting of objects (e.g. Host, User) and links (e.g. Is Administrator Of, Group Contains).
Every Tool operated feeds the Ledger and then Ontology, for continuous understanding. This rigorous data approach enables several outcomes:
- Cross control / domain workflows become possible where point products fall short; connect code, cloud, web, network, etc. inspection in a single workflow
- Streamlined analysis & reporting given a standard API for security data that is abstracted from underlying sources
- Change detection is possible with complete tracking of object changes over time
- Effective AI Agents is possible given this continuous mapping, similar to other forms of robotic autonomy
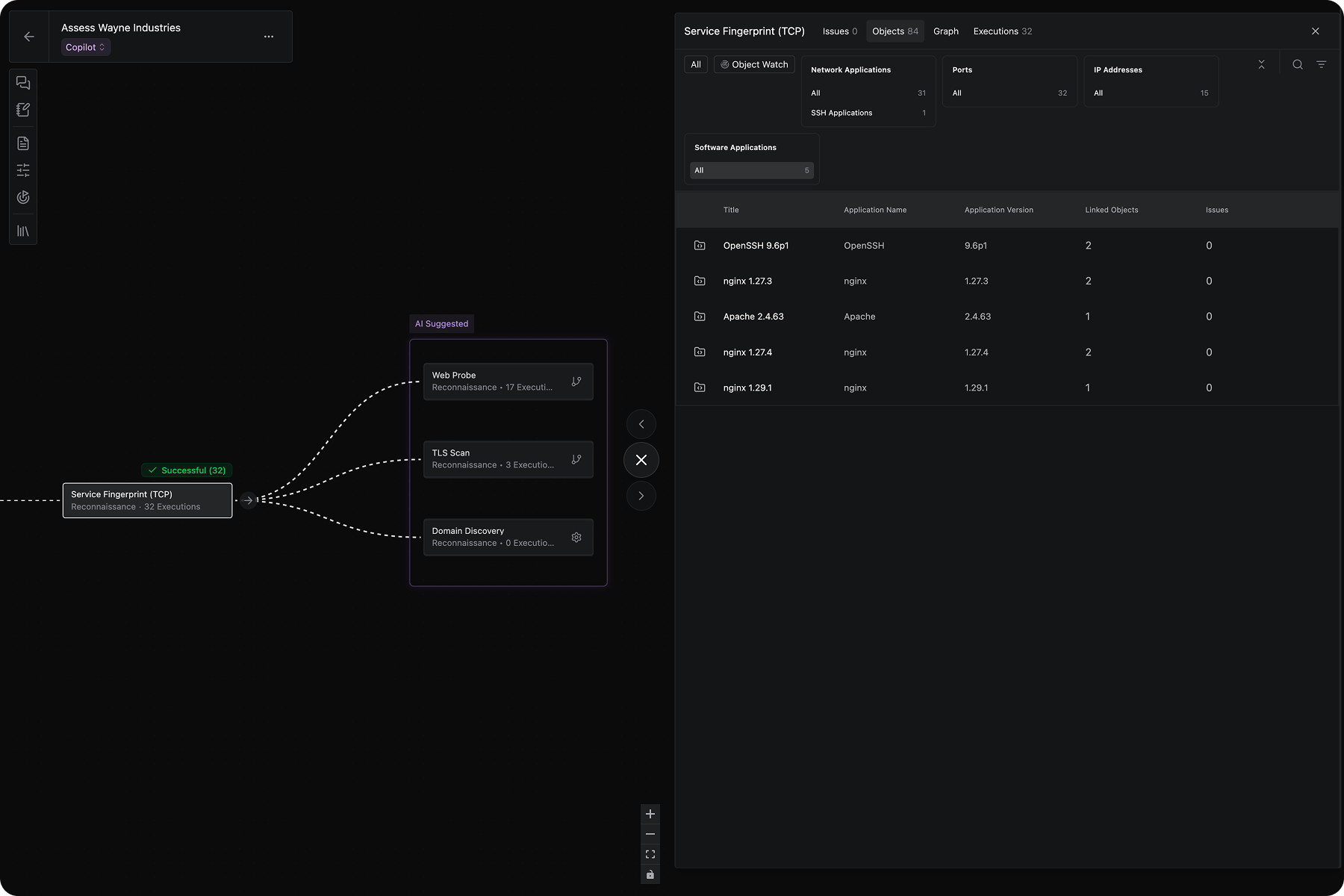
Deploy Any Tool, Everywhere
Method Platform is built on a Tool and security agent (codename: Jackal) framework that can functionally control any API, scanner, or custom CLI in the cloud or on-premise. This allows it to get both authenticated and unauthenticated sources to populate the Ontology and assume both defender and attacker perspectives. This also allows the platform to execute workflows in any environment for complete visibility across complex, multi-domain workflows.
Humans in control of AI
AI acts as a powerful enabler and force multiplier. In the high-stakes security domain, you must retain full control over AI agents for effective operational deployment. Method Platform incorporates rigorous guardrails and architectural safeguards to ensure you maintain complete authority over AI behavior and decision-making.