Use Entra ID for SSO
This guide will walk you through the process of creating an app in Entra ID and integrating it into Method Platform’s auth service for SSO. Under the hood Method Platform uses Keycloak as its auth service.
Setup Azure Entra ID
Navigate to Microsoft Entra ID
In the Microsoft Azure portal, click into Microsoft Entra ID.
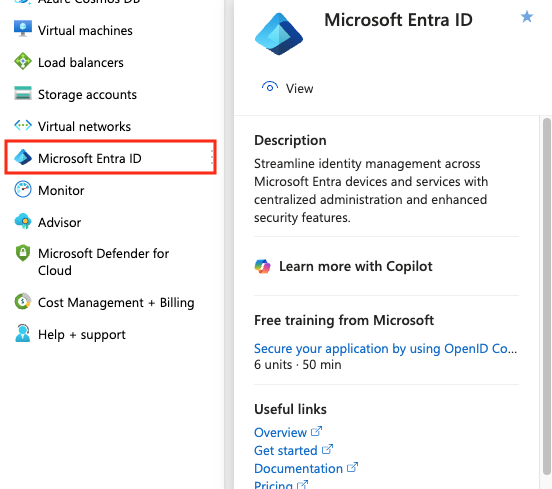
When you click on the menu, you’ll be to redirect to the tenant overview. If you don’t have any tenants, please see the Quickstart to create a new tenant.
Register a new Enterprise Application
On this page click Add and then Enterprise application.
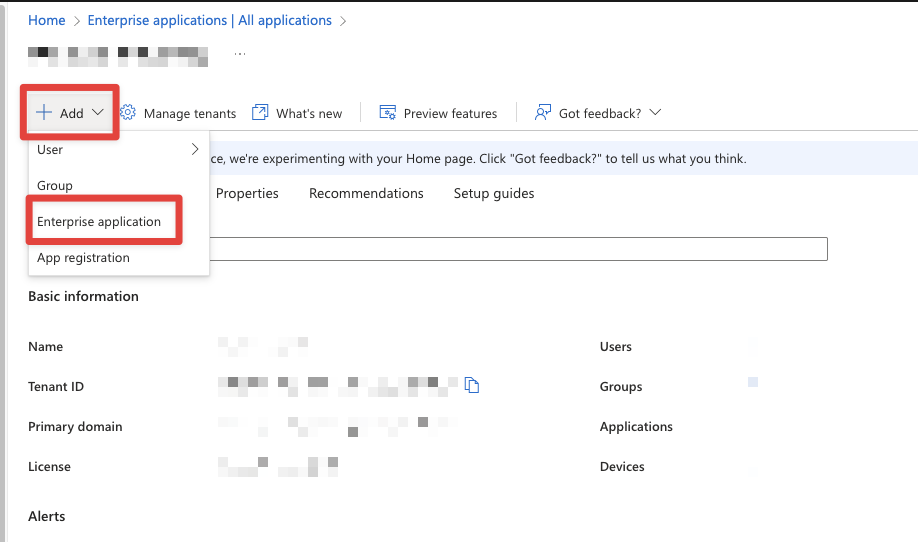
On the Browse Microsoft Entra App Gallery page, select Create your own application, and then Method Platform as the Name.

You should now see your Enterprise application within Entra. We will return here to set up SCIM, but for now, we need to set up our OIDC provider. To do this, in the left hand sidebar click on “App registrations”. You will see an app that shares the same name as the Enterprise application you just created. Once you click in, you’ll want to set up a redirect URI.
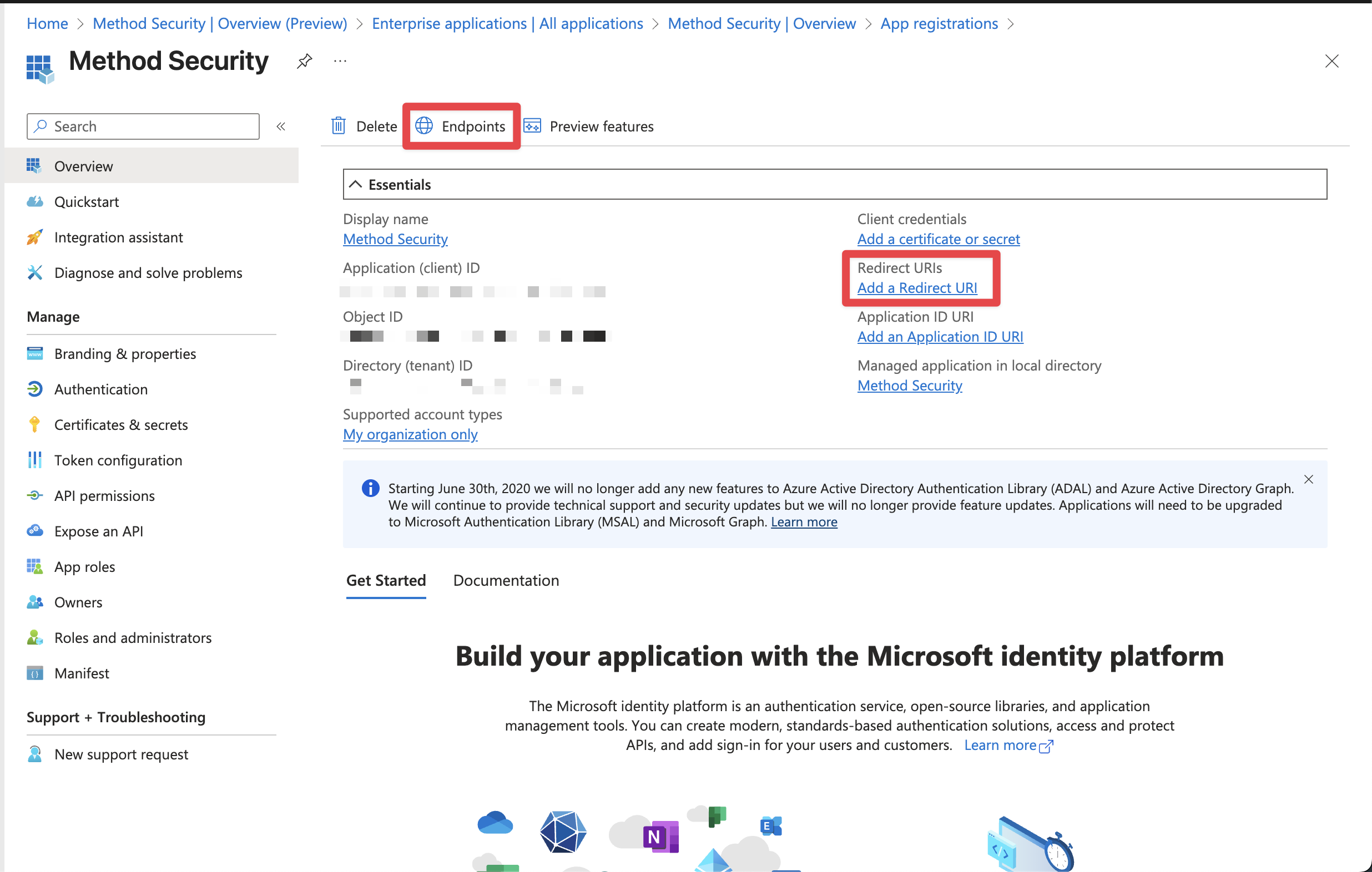
We will now configure our redirect URI:
Redirect URI
When prompted for your Redirect URI, enter https://keycloak.<codename>.method.delivery/realms/method/broker/entra/endpoint.
Codename
Make sure to replace <codename> in the URI above.
Create Client secrets
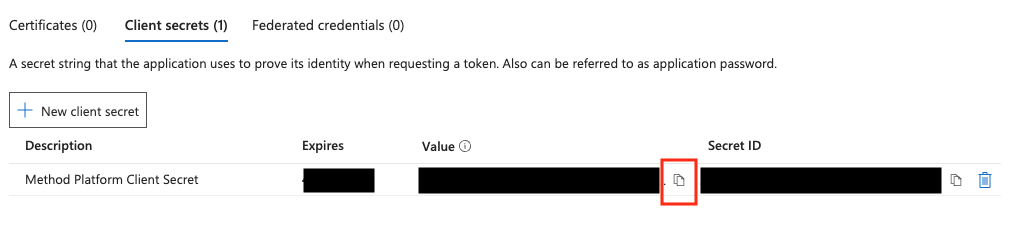
On the app overview page, select Add a certificate or secret or on the left sidebar select Certificates & secrets.
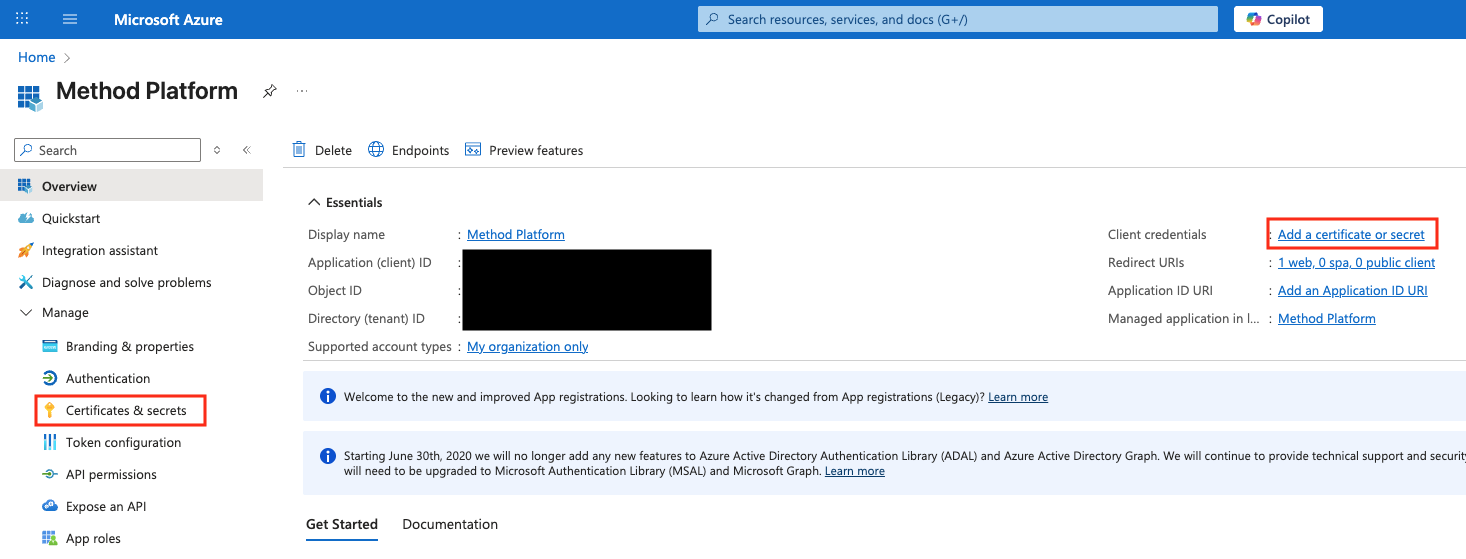
Next, select New client secret.
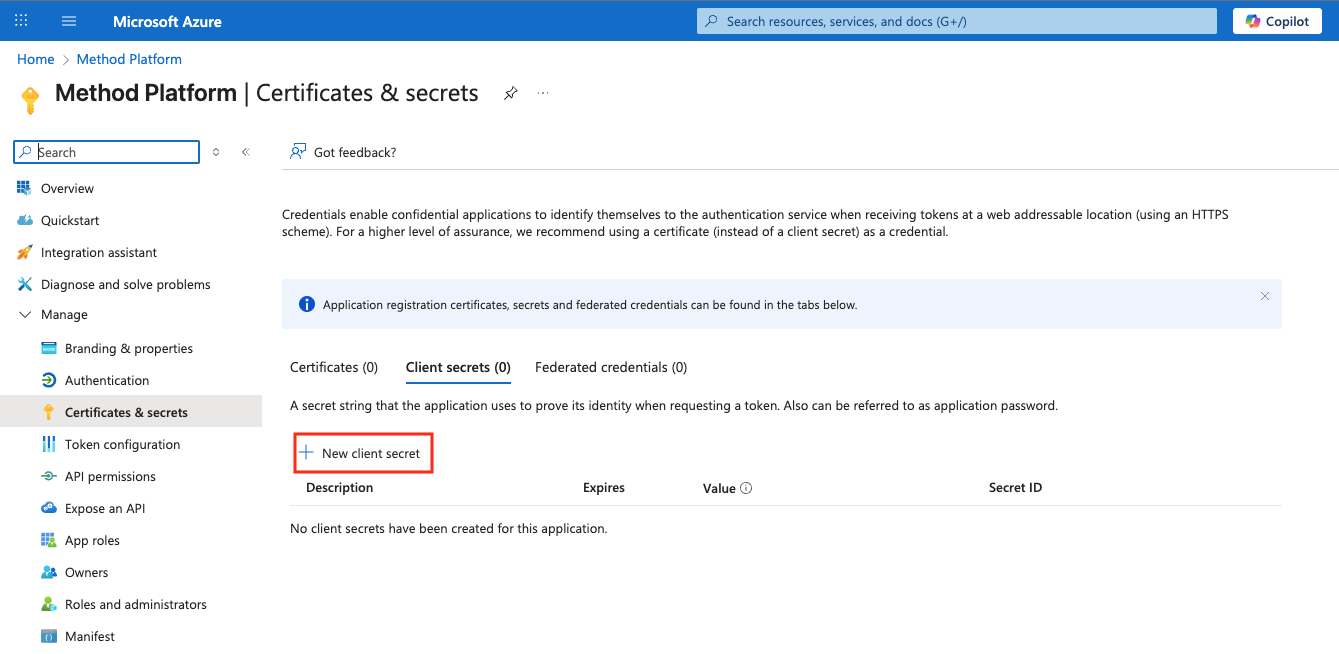
Fill out a description of Method Platform Client Secret and keep recommended 180 days.
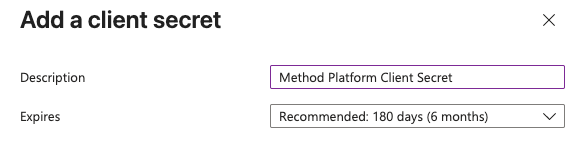
Copy the Value immediately because you will not be able to see this value again.
Share Information with your Method Mission Ops team
There will be three pieces of information you need to share with your Method Mission Ops team:
- The Client Secret copied in the previous step
- An endpoint URI with OpenID information
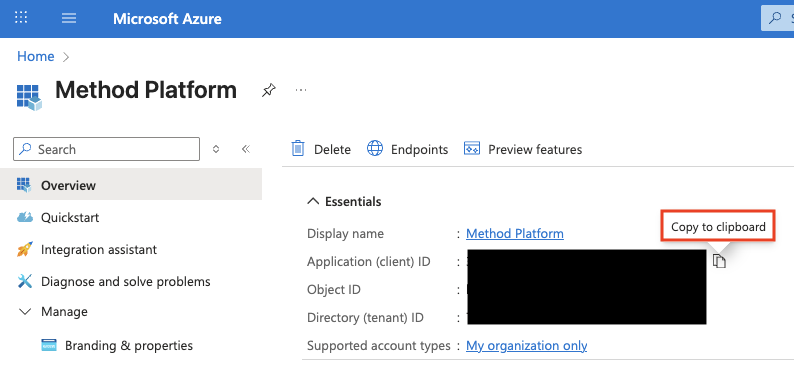
- Application (Client ID)
Get OpenID Endpoint URI
On the App main page, click Endpoints.
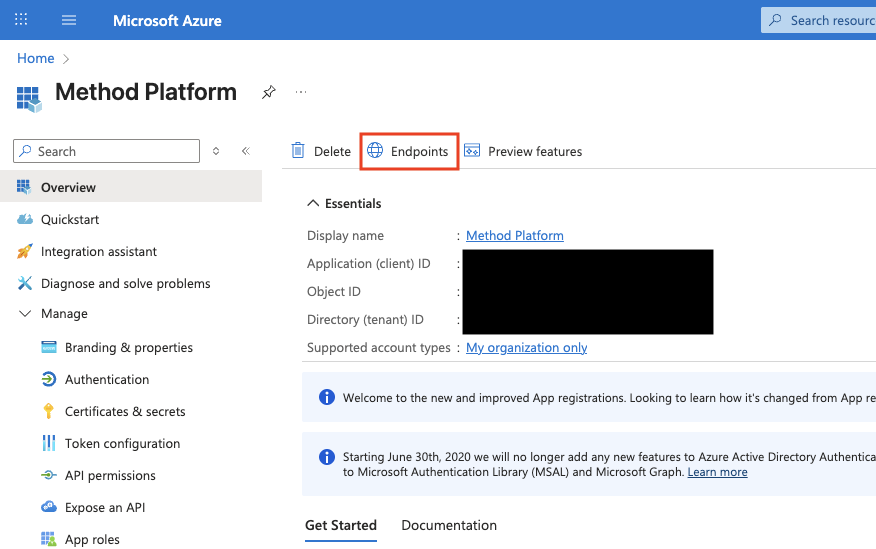
On the drawer that opens up, copy the value for OpenID Connect metadata document.

Get the Application (Client ID)
On the App main page, copy the value for Application (Client ID).
Send three pieces of information to Method Mission Ops team
Ensure that this information is sent securely.
Test login
Once you are notified by your Method Mission Ops team, you should see a new Entra option when logging into Method Platform.
SCIM
If you would like to configure SCIM, head back to your application under “Enterprise apps” in the left hand sidebar.
Once inside the application configuration, go to “Provisioning” and then click on “Connect your application”
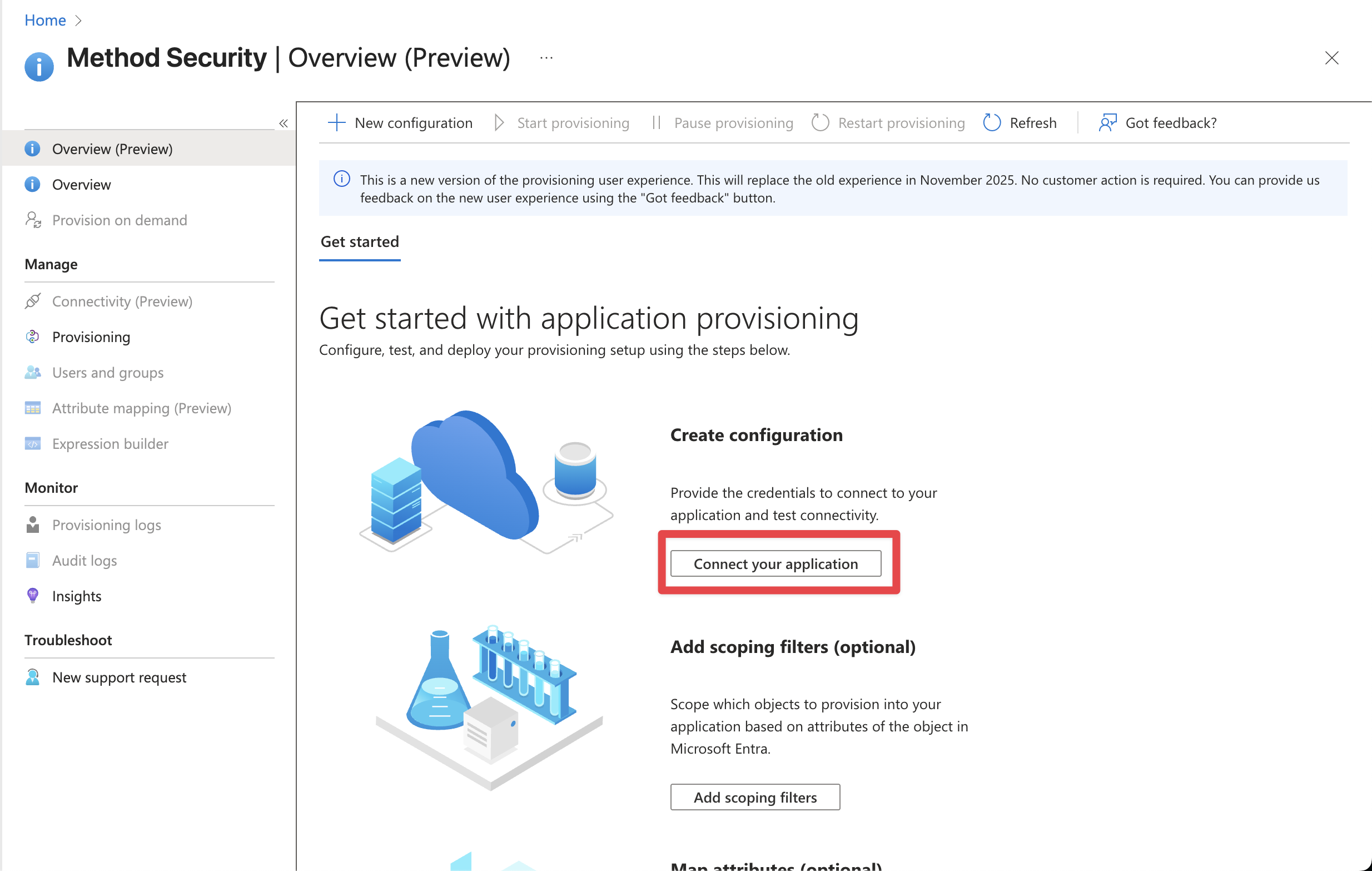
On the next screen, you’ll perform the following steps:
Tenant URL
Your URL will look like https://keycloak.<codename>.method.delivery/realms/method/scim/v2/organizations/<id>
Codename
Make sure to replace <codename> in the URI above.
Your Method Mission Operations team will share your tenant ID with you.
Attributes
Finally, we need to map our attributes to ensure that Method has the information it needs from the SCIM process to create users from Entra.
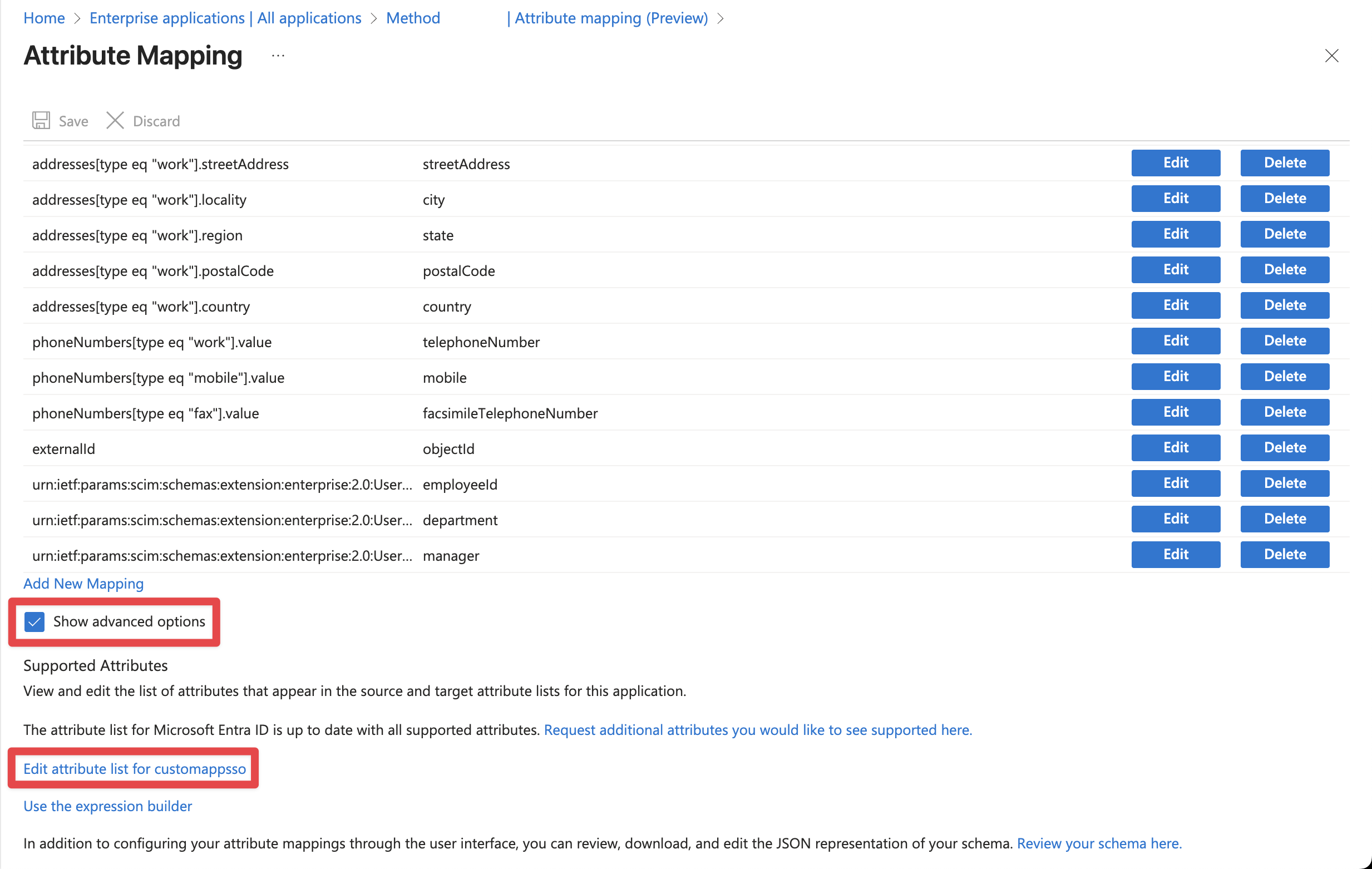
Share the attributes for mail, givenName, and surname with your Method Mission Operations team.