AWS Integration - CloudFormation
This guide will walk you through the process of running CloudFormation on either an individual AWS account or on your AWS Organization.
Prerequisites
Before you begin, ensure you have:
- AWS Account Access with permissions to create CloudFormation stacks
- For Single Account: CloudFormation and IAM permissions in the target account
- For AWS Organizations: Access to the Organization’s management account or delegated administrator permissions for StackSets
- OAuth Credentials: Client ID and Client Secret (provided by your Method Mission Operations Team)
- Method Domain: Your Method instance domain name
Overview
CloudFormation provides an easy way to quickly create resources within your AWS account. If you are using the AWS Organization feature within AWS, it also allows you to automatically apply a CloudFormation template to all accounts within your Organization or within specified Organizational Units (OUs). Method supports both of these operating models, allowing you to use CloudFormation to seamlessly integrate individual accounts, or entire Organizations with Method.
Method provides its CloudFormation templates in an open format to provide maximal transparency for your organization prior to applying them. You can find all of our templates in Github along with instructions on how to apply the templates.
What Gets Created
Both CloudFormation templates will create several resources within your AWS Account. For a detailed explanation, please refer to Github.
At a high level, a Lambda will be created that will leverage the provided OAuth credentials to authenticate with your Method instance and register a new IAM Role for your account. During this registration, a unique external ID will be generated that ensures your new IAM Role can only be accessed by Method. Once this Lambda completes, you will see the new IAM Role in your account.
Required Inputs
For both of these options, you will need the following pieces of information:
-
OAuth Client ID and Secret
-
These will be provided to you by your Method Mission Operations Team
Method is actively working on the ability for you to self-service create and manage OAuth Applications inside the Method Platform
-
-
Domain
- This is the domain name of your Method instance (e.g.,
company.method.security) - Do not include the
https://or any trailing slashes - You can find this in your browser’s address bar when logged into Method
- This is the domain name of your Method instance (e.g.,
Connecting an Individual Account
Applying the CloudFormation Template
AWS Console
AWS CLI
CloudFormation
In the AWS Console, search for “CloudFormation” in the top search bar and navigate to the CloudFormation page.
Upload
Select “Upload a template file”, click “Choose file”, and upload the method-integration.yaml file (download link above). Click “Next”.
Confirming Access
Now that the CloudFormation stack is complete, let’s verify the connection in Method:
Test Connectivity
Click the Test Connection button to verify the integration is working correctly.
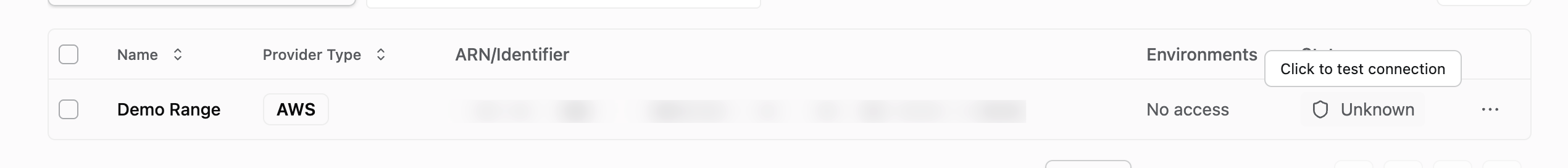
If there is an error, see the Troubleshooting section below or reach out to your Method Team for support.
Delegate to an Environment
To provide you with granular control over which Method Environments can leverage this new Cloud Connection, you must delegate access to individual Environments. This security measure ensures that only approved environments can use these AWS credentials.
From the Cloud Connection panel, search and select any environments you want to delegate to. You can also deselect or clear environments that you no longer want to provide access to.
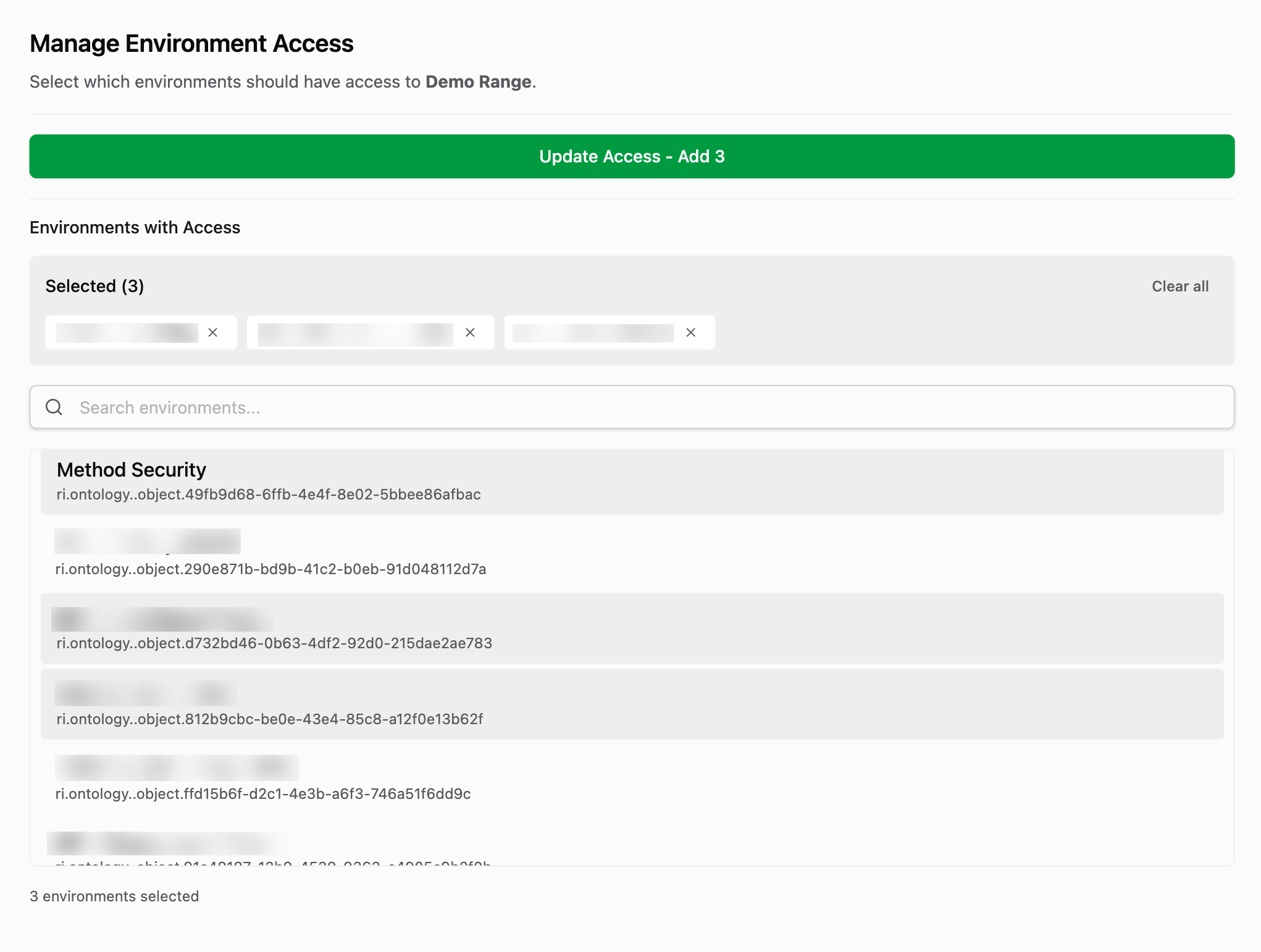
If you remove an environment from delegation, any scheduled or running Tasks in that environment using this connection will fail
What Happens Next
Once the connection is successfully tested and delegated:
- Method will begin discovering resources in your AWS account(s)
- You can create Tasks in delegated Environments that use this connection
- The connection will automatically renew using the IAM role created
- No further action is needed unless you want to modify the delegation
Connecting Multiple Accounts via AWS Organizations
If you want to provide Method with visibility into your entire AWS Organization or specific Organizational Units (OUs), you can use the Method StackSet CloudFormation template. This allows you to deploy the integration across multiple AWS accounts simultaneously, giving you full control over which accounts Method can access.
Additional Inputs
In addition to the three inputs mentioned above, you will need to determine if you would like to apply this template to every account in your Organization or only specified OUs. If you want to limit to certain OUs, you will need to have those values handy.
AWS Console
CloudFormation
In the AWS Console, search for “CloudFormation” in the top search bar and navigate to the CloudFormation page.
StackSets
From the left hand navigation panel, click “StackSets” and then the “Create StackSet” button.
Choose a template
Configure the following options:
- Permission model: Select “Service-managed permissions”
- Prepare Template: Select “Template is ready”
- Specify template: Choose one option:
- Upload the downloaded template file for review, OR
- Select “Amazon S3 URL” and enter:
https://method-cloudformation-templates.s3.us-east-1.amazonaws.com/aws/latest/method-stackset-template.yaml
Click “Next”
Details
Provide a name for your StackSet (e.g. MethodIamIntegration) and fill out the parameters for your OAuth Client ID, Client Secret, and Domain
Add Stacks
It is at this point that you will need to decide whether you want to deploy to your entire AWS Organization or to individual Organizational Units. Additionally, you’ll need to specify which Regions to deploy into. As Method is deploying an IAM role, it largely does not matter but it will determine which region the Lambda is run in.
Confirming Access
Now that the StackSet deployment is complete, let’s verify the connections in Method:
Test Connectivity
Click the Test Connection button for each account to verify the integration is working correctly.

If there is an error, see the Troubleshooting section below or reach out to your Method Team for support.
Delegate to an Environment
To provide you with granular control over which Method Environments can leverage these Cloud Connections, you must delegate access to individual Environments. This security measure ensures that only approved environments can use these AWS credentials.
From each Cloud Connection panel, search and select any environments you want to delegate to. You can also deselect or clear environments that you no longer want to provide access to.

If you remove an environment from delegation, any scheduled or running Tasks in that environment using this connection will fail
What Happens Next
Once the connections are successfully tested and delegated:
- Method will begin discovering resources in your AWS accounts
- You can create Tasks in delegated Environments that use these connections
- The connections will automatically renew using the IAM roles created
- No further action is needed unless you want to modify the delegation
Troubleshooting
Stack Creation Failed
- Check OAuth credentials: Verify you entered the correct Client ID and Client Secret
- Verify domain format: Ensure your domain doesn’t include
https://or trailing slashes (e.g., useyour.method.domainnothttps://your.method.domain/) - Check permissions: Ensure you have IAM permissions to create roles and Lambda functions
- Review stack events: In the CloudFormation console, check the Events tab for specific error messages
StackSet Deployment Failed
- Check Organization permissions: Ensure you have the necessary permissions in the Organization management account
- Review instance status: Check the Stack Instances tab for specific accounts that failed
- Verify OU IDs: If targeting specific OUs, confirm the OU IDs are correct
- Region availability: Ensure the selected regions support the required services
Connection Test Failed in Method
- Wait for completion: Allow 2-3 minutes after stack creation for the Lambda to complete execution
- Check CloudFormation status: Verify the stack shows CREATE_COMPLETE in the CloudFormation console
- Verify IAM role: Confirm the IAM role was created successfully in the IAM console
- Review CloudWatch logs: Check the Lambda function logs in CloudWatch for any errors during registration
Connection Lost After Working
- Check IAM role: Verify the IAM role hasn’t been deleted or modified
- Review permissions: Ensure the role’s trust policy hasn’t changed
- Check organization changes: For StackSets, verify accounts haven’t been moved or removed from targeted OUs
Need Help?
If you’re still experiencing issues, reach out to your Method Team with:
- CloudFormation stack ID or StackSet name
- Error messages from the Events tab or Stack Instances tab
- Screenshots of any failures
- AWS account ID(s) affected
Deep Dive
For a deep dive into the templates, additional parameters they provide, and more, please see our Github.