AWS Integration - Terraform
This guide will walk you through the process of running Terraform on either an individual AWS account or on your AWS Organization.
Overview
Terraform provides a declarative way to manage infrastructure as code within your AWS accounts. If you are using AWS Organizations, Terraform also allows you to automatically deploy resources across multiple accounts within your Organization. Method supports both of these operating models, allowing you to use Terraform to seamlessly integrate individual accounts or entire Organizations with Method.
Method provides its Terraform modules in an open format to provide maximal transparency for your organization prior to applying them. You can find all of our modules in Github along with instructions on how to apply the modules.
What Gets Created
Both Terraform modules will create several resources within your AWS Account. For a detailed explanation, please refer to Github.
At a high level, a Lambda will be created that will leverage the provided OAuth credentials to authenticate with your Method instance and register a new IAM Role for your account. During this registration, a unique external ID will be generated that ensures your new IAM Role can only be accessed by Method. Once this Lambda completes, you will see the new IAM Role in your account.
Required Inputs
For both of these options, you will need the following pieces of information:
-
OAuth Client ID and Secret
-
These will be provided to you by your Method Mission Operations Team
Method is actively working on the ability for you to self-service create and manage OAuth Applications inside the Method Platform
-
-
Domain
- This is the domain name of your Method instance. Do not include the
https://or any trailing slashes
- This is the domain name of your Method instance. Do not include the
Connecting an Individual Account
Applying the Terraform Module
Using the Module
Direct Apply
Create a new Terraform configuration file (e.g., main.tf) with the following content:
Create a variables.tf file:
Create a terraform.tfvars file with your values:
Confirming Access
Back in the Method Platform, in the Admin -> Integrations panel, it’s time to confirm our access.
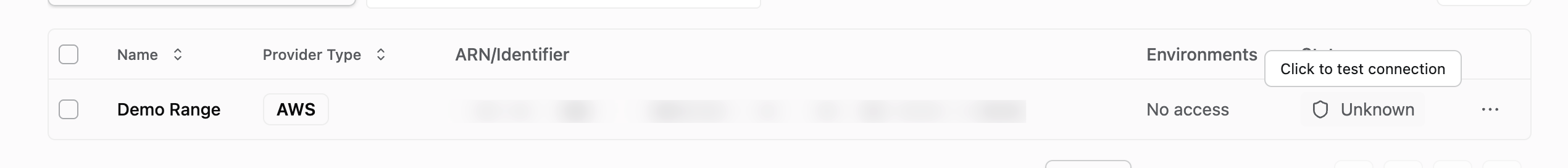
Test Connectivity
Confirm the connection was successful by clicking the Test Connection button. If there is an error, please reach out to your Method Team for support.
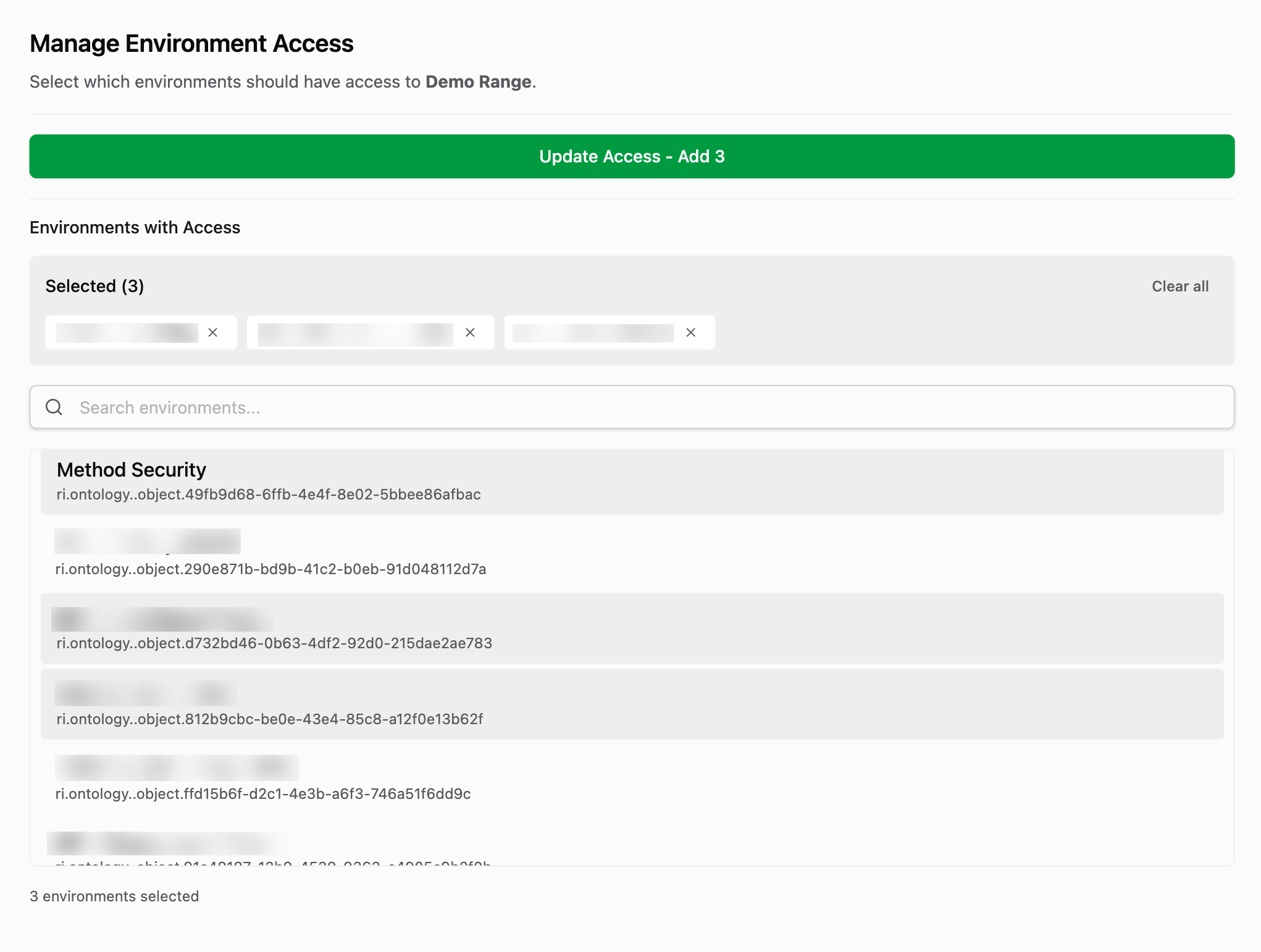
Delegate to an Environment
To provide you with granular control over which Method Environment’s are able to leverage this new Cloud Connection, you need to delegate that ability to individual Environments.
From the Cloud Connection panel, search and click for any additional environments you want to delegate to. You can also deselect or clear environments that you no longer want to provide access to.
Connecting Multiple Accounts via AWS Organizations
Instead, if you want to provide Method with visibility to your entire AWS Organization or a subset of accounts, you can use the Method StackSet Terraform module to deploy across multiple accounts within your Organization.
Prerequisites
To use the StackSet module, you’ll need:
- AWS CLI configured with appropriate credentials
- Terraform installed (version 1.0 or higher)
- Access to your AWS Organization’s management account or appropriate delegated administrator permissions
- Depending on your deployment strategy:
- For entire organization: Organization-level permissions
- For specific OUs: The Organizational Unit IDs you want to target
- For specific accounts: The list of AWS account IDs you want to integrate with Method
Applying the Terraform Module
Create your variables.tf and terraform.tfvars files as shown in the single account section above, then create a new Terraform configuration file (e.g., main.tf):
Entire Organization
Specific OUs
Specific Accounts
Deploy to all accounts in your AWS Organization:
This will automatically deploy to all accounts in your Organization, including future accounts as they are added.
Confirming Access
Back in the Method Platform, in the Admin -> Integrations panel, it’s time to confirm our access.
Test Connectivity
Confirm the connection was successful by clicking the Test Connection button. If there is an error, please reach out to your Method Team for support.

Delegate to an Environment
To provide you with granular control over which Method Environment’s are able to leverage this new Cloud Connection, you need to delegate that ability to individual Environments.
From the Cloud Connection panel, search and click for any additional environments you want to delegate to. You can also deselect or clear environments that you no longer want to provide access to.

Deep Dive
For a deep dive into the Terraform modules, additional variables they provide, and more, please see our Github.